Contents
Sizing Guide
To obtain and maintain optimum performance under varying operational conditions of the program, you must take into account the number of networked devices, network topology, and the set of program features that you need.
Selection of the optimal program configuration consists of the following steps:
Common scenarios for deployment and installation of program components
The scenario for deployment and installation of program components is determined by the planned load on the program servers.
Kaspersky Endpoint Agent can be installed on any computers that belong to the organization's IT infrastructure and run the Windows operating system. Outbound connections from computers with Kaspersky Endpoint Agent to the server hosting the Central Node component must be allowed directly, without a proxy server.
You can install one or multiple Central Node components. If you install multiple Central Node components, you can use them independently of each other or combine them for centralized management in distributed solution mode.
The deployment scenario selection depends on the utilized program functionality. All scenarios listed in this manual also apply to the deployment of the program on a virtual platform.
Full functionality (KATA and KEDR)
When using KATA and KEDR functionality, you can scan network traffic, mail traffic, and data on corporate LAN computers.
If more than 5000 Kaspersky Endpoint Agent programs are installed within the organization, it is not recommended to use the Central Node component to process traffic.
You can use the Sensor component as a proxy server for connecting hosts to Kaspersky Endpoint Agent and the Central Node. One Sensor component supports the connection of up to 1000 Kaspersky Endpoint Agent hosts.
The criteria for selecting a deployment scenario when using KATA and KEDR functionality are presented in the table below. The selection algorithm is as follows:
- In each row of the table, select the cell containing the value of the criterion corresponding to your IT infrastructure.
If a row contains two cells with identical values, you must select the cell on the left.
- Select the right-most column in which there are marked cells.
Selecting a deployment scenario when using KATA and KEDR functionality
Criterion
Two-server scenario
Three-server scenario
Four- or more server scenario
Network traffic and mail traffic cannot be received on the same device.
No
Yes
Yes
Yes
Number of Kaspersky Endpoint Agent hosts
No
From 5000 to 10,000
From 5000 to 10,000
Over 10,000
1 Gbps
From 1 to 2 Gbps
Over 2 Gbps
Over 2 Gbps
The number of remote infrastructures in which traffic needs to be analyzed.
No
One
Two or more
Two or more
The capacities of one Sandbox component are insufficient to analyze all objects within acceptable time frames.
No
No
Yes
Yes
In distributed solution mode each program component must meet the hardware requirements specified in the sizing calculator.
Processing of network traffic, mail traffic, and web traffic (KATA)
It is recommended to use KATA functionality if the organization does not need to process data on corporate LAN computers. If this is the case, only network traffic and mail traffic are processed.
The criteria for selecting a deployment scenario when using KATA functionality are presented in the table below. The selection algorithm is as follows:
- In each row of the table, select the cell containing the value of the criterion corresponding to your IT infrastructure.
If a row contains two cells with identical values, you must select the cell on the left.
- Select the right-most column in which there are marked cells.
Selecting a deployment scenario when using KATA functionality
Criterion
Two-server scenario
Three-server scenario
Four- or more server scenario
Network traffic and mail traffic cannot be received on the same device.
No
Yes
Yes
1 Gbps
From 1 to 2 Gbps
Over 2 Gbps
The number of remote infrastructures in which traffic needs to be analyzed.
No
One
Two or more
The capacities of one Sandbox component are insufficient to analyze all objects within acceptable time frames.
No
No
Yes
Processing of data from corporate LAN computers (KEDR)
It is recommended to use KEDR functionality if the organization does not need to process traffic. If this is the case, only data on corporate LAN computers is processed.
Depending on the presence of a third-party Sandbox solution within the organization, you can use one of the following deployment scenarios:
- Without a Sandbox component
- With a Sandbox component
Two-server deployment scenario.
When using KATA and KEDR functionality, you can install the Kaspersky Endpoint Agent program on corporate LAN computers. When using KATA functionality, the Kaspersky Endpoint Agent program is not installed.
When using this deployment scenario, the Central Node and Sensor components are installed on the same server or cluster. This server or cluster receives traffic, performs an initial analysis of traffic and a deeper analysis of extracted files. Based on the scan results, components detect signs of targeted attacks on the organization's IT infrastructure.
The Sandbox component is installed on the other server.
The scenario for program operation when deployed on two servers is presented in the figure below.
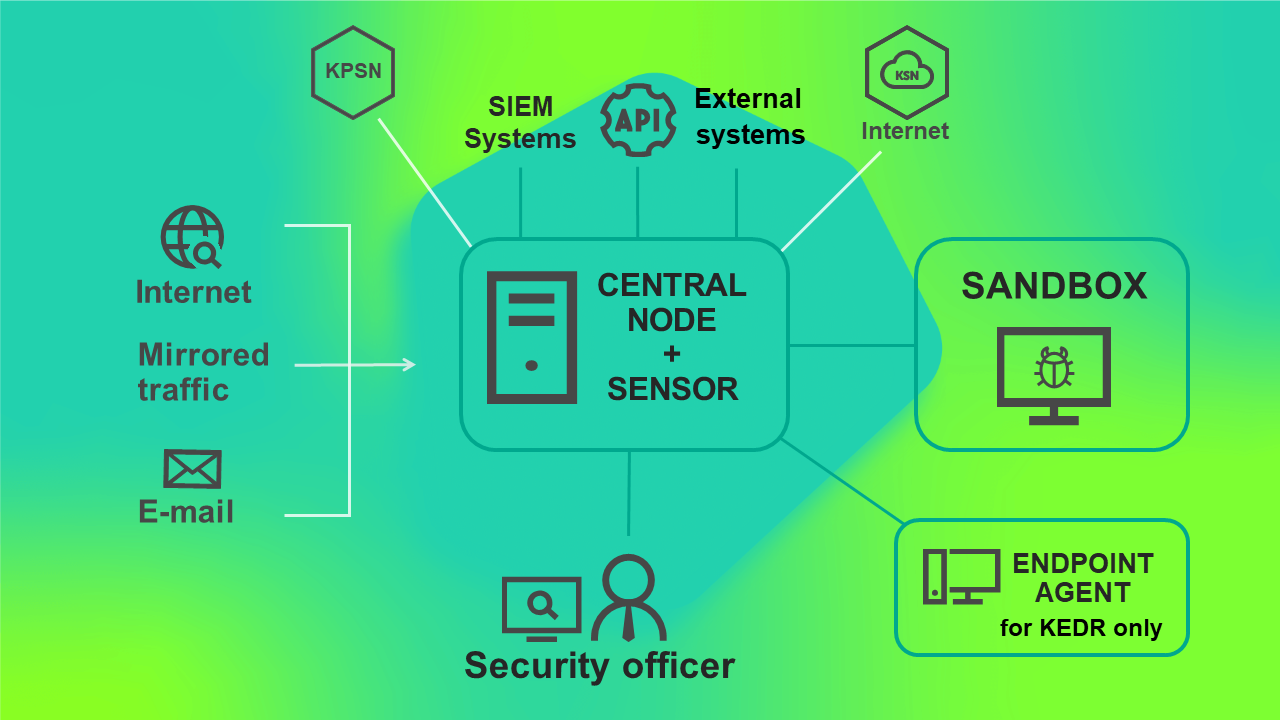
Program operating scenario when deployed on two servers
Three-server deployment scenario.
When using KATA and KEDR functionality, you can install the Kaspersky Endpoint Agent program on corporate LAN computers. When using KATA functionality, the Kaspersky Endpoint Agent program is not installed.
When using this deployment scenario, the Sensor, Central Node and Sandbox components are installed on separate servers. The Central Node component can also be deployed as a cluster. The server with the Sensor component receives traffic, performs an initial analysis, extracts files and forwards them to the Central Node component for a deeper analysis.
Using this deployment scenario, the Central Node component can receive traffic and perform an initial analysis of data in the main infrastructure. In this case, you can install the Sensor component on a server of a remote infrastructure whose traffic needs to be analyzed. If the channel bandwidth in the main infrastructure is more than 2 Gbps, you are advised to install the server with the Sensor component in the main infrastructure.
The traffic exchanged between the Central Node and Sensor components comprises up to 20% of traffic received by the Sensor component.
The program operating scenario when deployed on three servers is presented in the figure below.
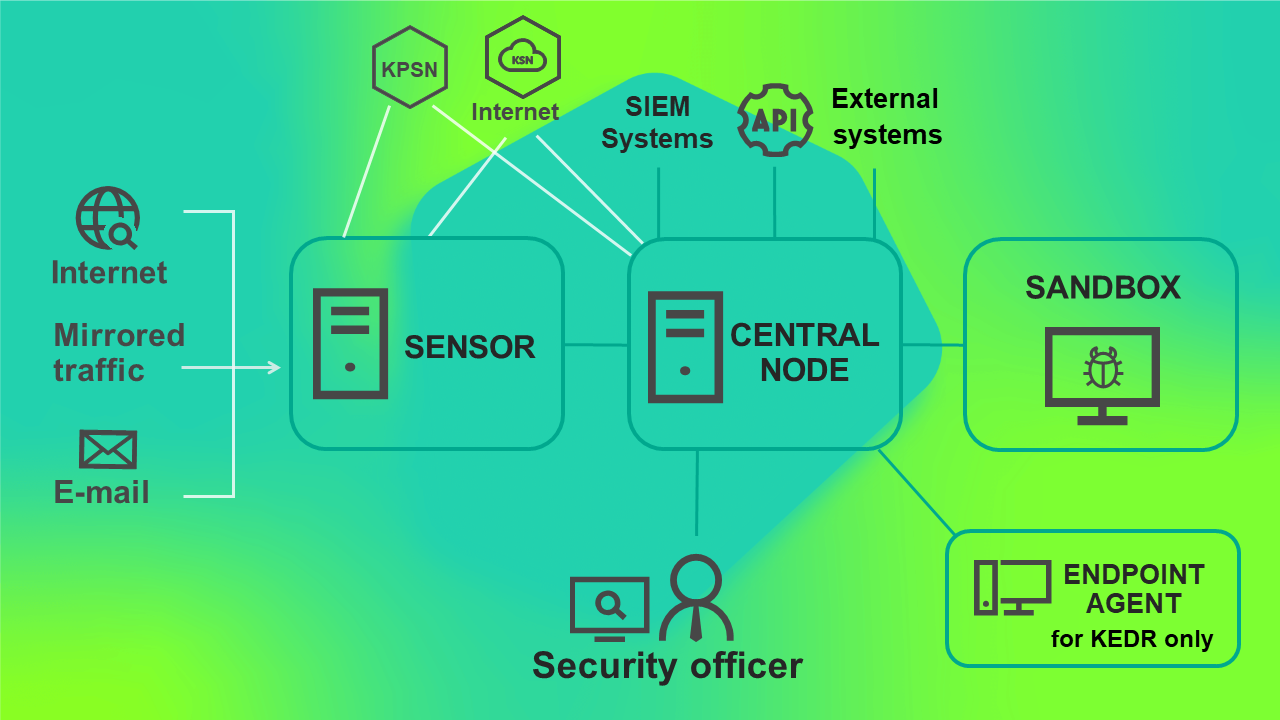
Program operating scenario when deployed on three servers
Scenario of deployment on four or more servers.
When using KATA and KEDR functionality, you can install the Kaspersky Endpoint Agent program on corporate LAN computers. When using KATA functionality, the Kaspersky Endpoint Agent program is not installed.
If there is a large volume of traffic, you can install multiple Sensor components or multiple Sandbox components on different servers. This scenario is recommended for deployment in large organizations.
You can also use one Sandbox component to connect to multiple Central Node components.
The operating schematic of the program when deployed on four or more servers is presented in the figure below.
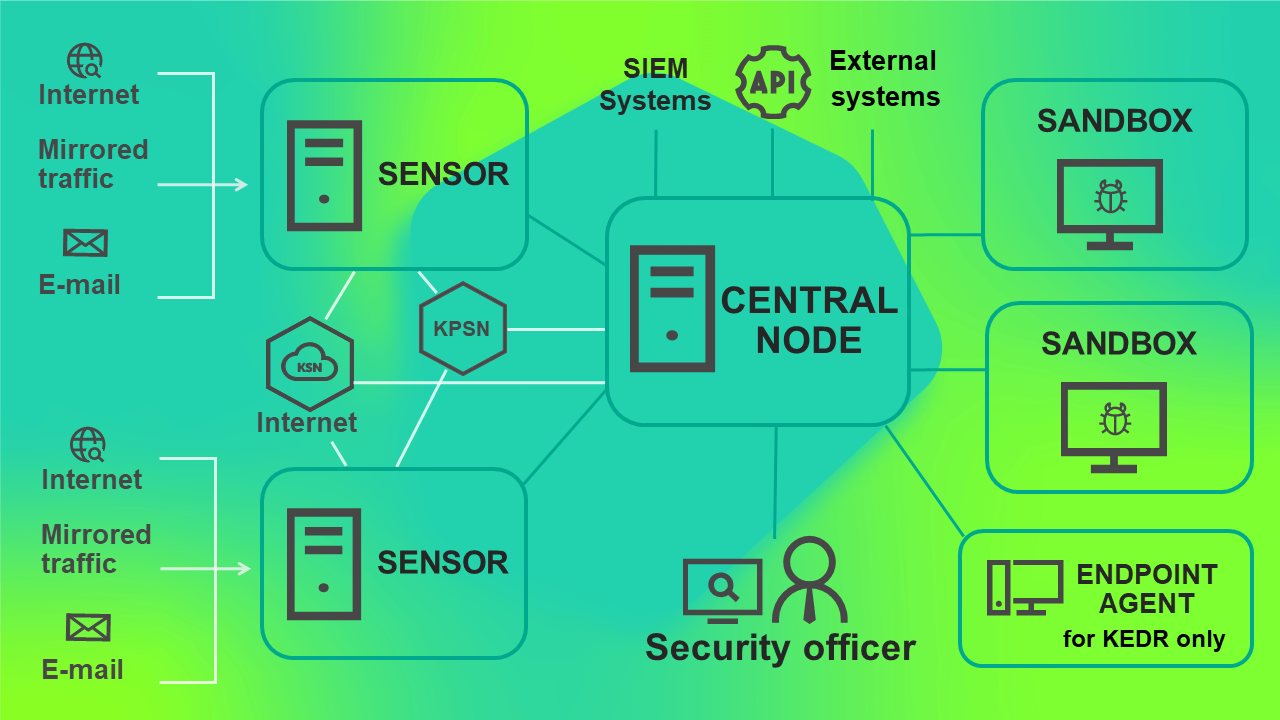
Program operating scenario when deployed on four or more servers
Scenario for deploying KEDR functionality with a Sandbox component.
Using this deployment scenario, you need to install the Central Node component separately from the Sensor component.
The program operating scenario when deploying KEDR functionality with the Sandbox component is presented in the figure below.
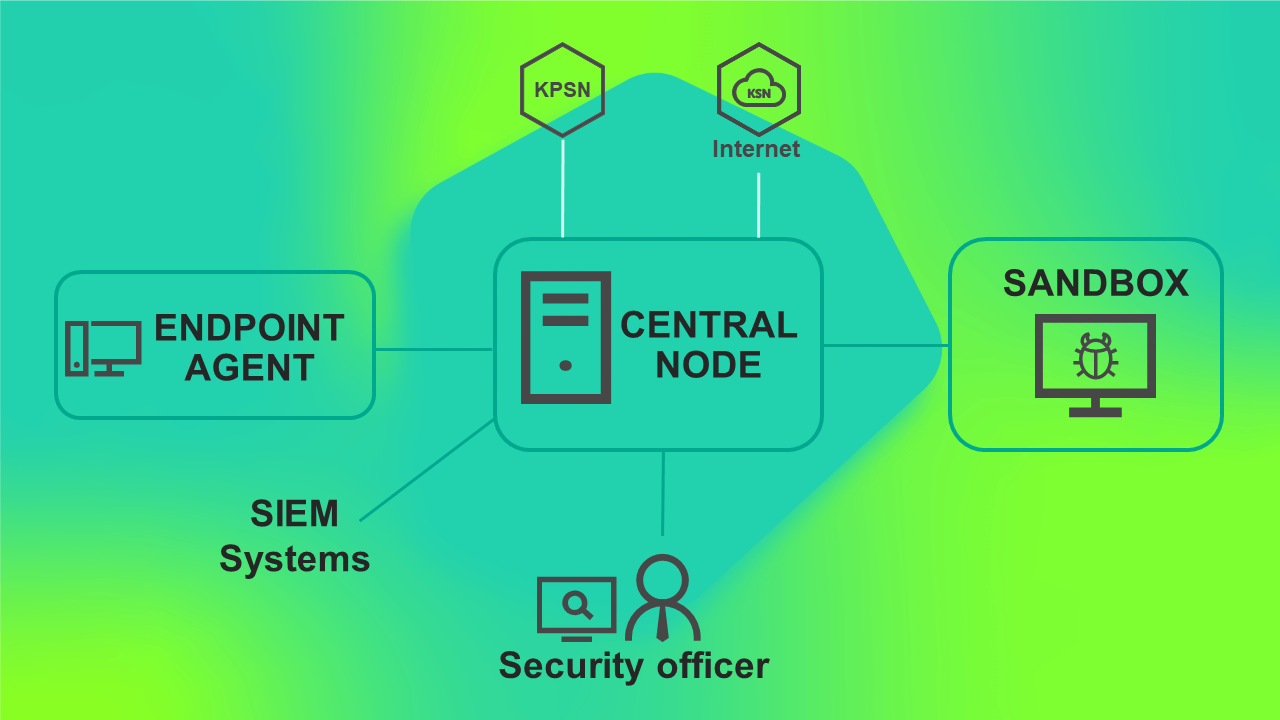
Program operating scenario when deploying KEDR functionality with the Sandbox component
Scenario for deploying KEDR functionality without a Sandbox component.
You do not need to install the Sandbox component and can use the Central Node component only for managing the Kaspersky Endpoint Agent program and data analysis.
Using this deployment scenario, you need to install the Central Node component separately from the Sensor component.
The program operating scenario when deploying KEDR functionality without the Sandbox component is presented in the figure below.
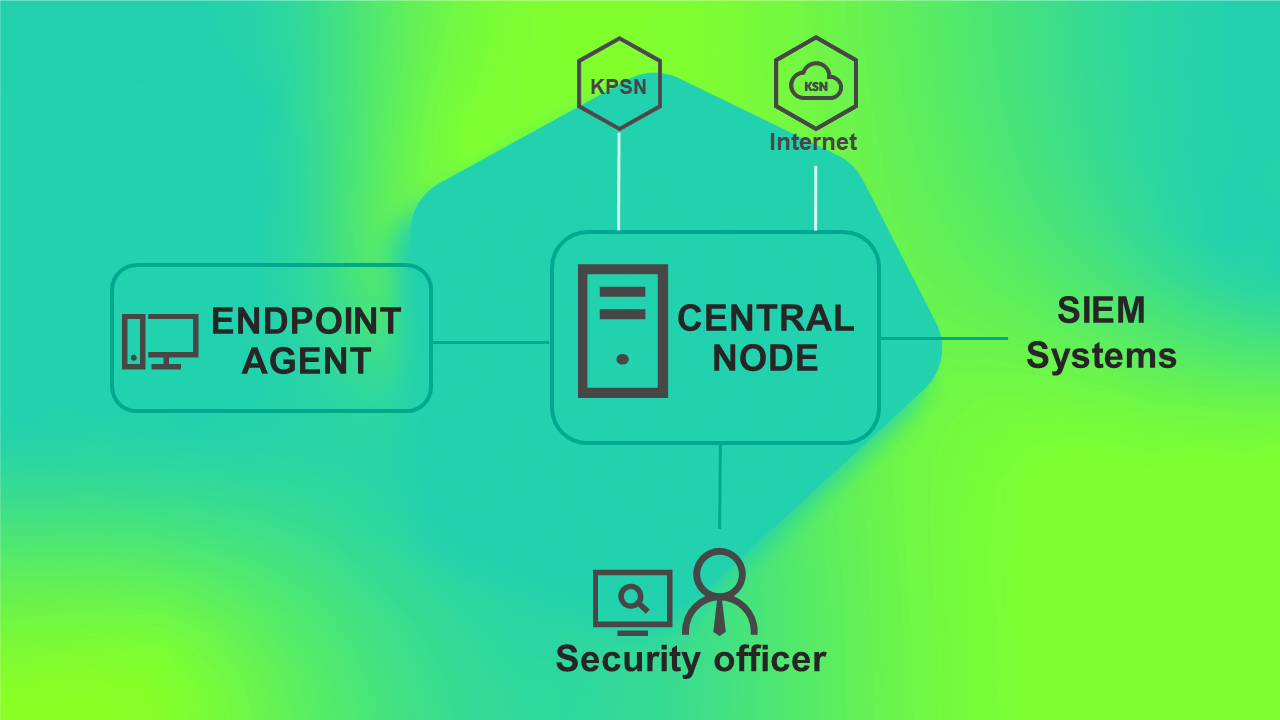
Program operating scenario when deploying KEDR functionality without the Sandbox component
Sizing calculator
After you have selected the deployment scenario that is most appropriate for your IT infrastructure, you must calculate the hardware requirements for servers used for installing program components.
Calculations for the Sensor component
These calculations also apply when the program is deployed on a virtual platform.
When calculating the hardware requirements for the Sensor component, you must take into account that the maximum volume of processed traffic for one Sensor component is 4 Gbps. The most resource-intensive technology is the Intrusion Detection System.
You can use a server hosting the Sensor component as a proxy server during data exchange between Kaspersky Endpoint Agent and the Central Node component to simplify configuration of network rules. For example, if Kaspersky Endpoint Agent computers are located on a separate segment of the network, it will suffice to configure a connection between servers with the Central Node and Sensor components.
When configuring the forwarding of Kaspersky Endpoint Agent traffic to the Central Node component, the following limitations apply:
- A maximum of 15,000 Kaspersky Endpoint Agent computers can connect to a single Central Node component.
- The maximum allowed packet loss between servers hosting the Sensor and Central Node components should be 10% with a packet delay up to 100 ms.
The hardware requirements for a server with the Sensor component depend on the volume of processed traffic. The required bandwidth of the communication channel between servers with the Central Node and Sensor components is the sum of the traffic of the Sensor component (10% of the traffic at the SPAN port + mail traffic + traffic over the ICAP protocol) and the requirements of the communication channel between the Central Node component and Kaspersky Endpoint Agent components (depending on the number of Kaspersky Endpoint Agent computers whose traffic the Sensor component redirects to the Central Node component).
When calculating hardware requirements for the server with the Sensor component, please keep in mind that one instance of Kaspersky Endpoint Agent for Linux generates the same load as three instances of Kaspersky Endpoint Agent for Windows.
If the bandwidth of the communication channel is more than 2 Gbps, you must configure the use of one processor core for processing network interrupts.
Hardware requirements for the Sensor component depending on the processed traffic
The Sensor component can be integrated with the IT infrastructure of an organization as follows:
- Receive mirrored traffic from network devices from SPAN ports.
- Connect to a mail server over the POP3 protocol.
- Connect to a mail server over the SMTP protocol.
- Receive traffic from a proxy server over the ICAP protocol.
The hardware requirements for the Sensor component are listed in the table below. The calculations are provided for a case in which the Sensor component does not process email messages or traffic over the ICAP protocol. If the Sensor component forwards traffic from Kaspersky Endpoint Agent computers, link requirements must also be taken into account.
Hardware requirements for the Sensor component depending on the volume of processed traffic from SPAN ports
Maximum number of Kaspersky Endpoint Agent for Windows computers |
Maximum volume of processed traffic (Mbps) |
Minimum RAM (GB) |
Minimum number of logical cores |
|---|---|---|---|
10000 |
100 |
16 |
4 |
15000 |
500 |
16 |
8 |
15000 |
1000 |
24 |
16 |
15000 |
2000 |
32 |
32 |
15000 |
4000 |
32 |
48 |
The hardware requirements for a Sensor component that is integrated with a mail server are presented in the table below. The calculations are provided for a case in which the Sensor component does not process mirrored traffic or traffic over the ICAP protocol.
Hardware requirements for a Sensor component that is integrated with a mail server
Maximum number of email messages per second |
Minimum RAM (GB) |
Minimum number of logical cores |
|---|---|---|
1-4 |
16 |
4 |
5-20 |
16 |
8 |
Processing traffic over the ICAP protocol requires less resources than processing email messages.
If the same Sensor component is used to process different protocol traffic, keep in mind the following recommendations:
- Simultaneous processing of traffic over the ICAP protocol and from SPAN ports is recommended for analysis of objects transmitted through a proxy server over the HTTPS protocol.
To process traffic over the HTTPS protocol, the proxy server must support server certificate replacement.
- When integration with mail sensors is configured, it is not practical to extract SMTP traffic from SPAN traffic.
Disk space requirements on a server with the Sensor component
It is recommended to use a RAID 1 disk array. The total disk space must be at least 500 GB. The minimum free disk space requirements for different data types are presented in the table below.
Minimum requirements for disk space on a server with the Sensor component
Data type |
Disk space (GB) |
|---|---|
Redis database dump |
16 |
Operating system |
25 |
Temporary files |
32 |
Trace files and update packages |
151 |
Total |
224 |
If the volume of processed traffic is greater than 1 Gbps, it is recommended to allocate at least 600 GB of disk space.
Calculations for the Central Node component
If the program is deployed to a virtual platform, CPU resource requirements are to be increased by 10 percent. In virtual disk settings, a Thick Provision disk type must be selected.
To avoid possible performance degradation when deploying the application on a virtual platform, we recommend to:
- Set Latency Sensitivity to High.
- Reserve all memory.
- Reserve all CPU.
Hardware requirements for a server with the Central Node and Sensor components
The hardware requirements for a server on which the Central Node and Sensor components are installed depend on the following conditions:
- Volume of processed traffic
- Number of email messages processed per second.
- Number of Kaspersky Endpoint Agent hosts.
Kaspersky Endpoint Agent can be installed on a terminal server, file server, or network attached storage (NAS).
If Kaspersky Endpoint Agent is installed on a terminal server, the load generated by the component is calculated as follows: one Kaspersky Endpoint Agent program on a terminal server serving X users generates the same load as X Kaspersky Endpoint Agent programs on a host (X users = X Kaspersky Endpoint Agent programs).
If Kaspersky Endpoint Agent is installed on a file server or NAS, the load generated by the component is calculated as follows: one Kaspersky Endpoint Agent program on a file server or NAS generates the same load as 20 Kaspersky Endpoint Agent programs on a host.
When calculating the number of hosts with Kaspersky Endpoint Agent, please keep in mind that one instance of Kaspersky Endpoint Agent for Linux generates the same load as three instances of Kaspersky Endpoint Agent for Windows.
Kaspersky Endpoint Agent for Windows can also be installed on a SCADA server.
If Kaspersky Endpoint Agent for Windows is installed on a SCADA server, the load generated by the program is calculated as follows: one Kaspersky Endpoint Agent for Windows program on a SCADA server generates the same load as 20 Kaspersky Endpoint Agent for Windows programs on a host.
You can use Kaspersky Endpoint Agent for Linux and Kaspersky Endpoint Agent for Windows simultaneously.
If the volume of processed traffic is greater than 1 Gbps, it is recommended to install Central Node and Sensor components on separate servers.
On the server with the Central Node component, it is recommended to use two RAID disk subsystems:
- The first RAID 1 or RAID 10 disk subsystem is used for all the data specified in the table below, except for the Targeted Attack Analyzer database.
- The second RAID 10 disk subsystem is used for the Targeted Attack Analyzer database and for storing some of the logs.
Kaspersky Anti Targeted Attack Platform does not support operation with software RAID array.
The hardware requirements for the server with the Central Node component depending on the utilized functionality are presented in the table below.
Hardware requirements for the server with the Central Node component when using KEDR functionality
Maximum number of Kaspersky Endpoint Agent for Windows hosts |
Minimum RAM (GB) |
Minimum number of logical cores at 3 GHz |
First disk subsystem |
Second disk subsystem |
||||||
|---|---|---|---|---|---|---|---|---|---|---|
ROPS (read operations per second) |
WOPS (write operations per second) |
RAID disk array size (TB) |
The number of disks in a RAID disk array |
ROPS (read operations per second) |
WOPS (write operations per second) |
RAID disk array size (TB) |
The number of disks in a RAID disk array |
|||
1000 |
64 |
8 |
100 |
1000 |
1 |
4 |
300 |
200 |
Depends on the preferred storage policy |
4 |
3000 |
80 |
12 |
100 |
1000 |
1 |
4 |
700 |
500 |
6 |
|
5000 |
96 |
12 |
100 |
1000 |
1 |
4 |
1000 |
600 |
6 |
|
10,000 |
160 |
20 |
100 |
1000 |
1 |
4 |
2000 |
800 |
10 |
|
15,000 |
192 |
32 |
100 |
1000 |
1 |
4 |
2000 |
800 |
12 |
|
Hardware requirements for the server with the Central Node component when using KATA and KEDR functionality
Maximum number of Kaspersky Endpoint Agent for Windows hosts |
Maximum number of email messages per second |
Maximum volume of traffic from SPAN ports on the server with the Central Node component |
Maximum volume of traffic from SPAN ports on servers with the Sensor component (Mbps) |
Minimum RAM (GB) |
Minimum number of logical cores at 3 GHz |
First disk subsystem |
Second disk subsystem |
||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
ROPS (read operations per second) |
WOPS (write operations per second) |
RAID disk array size (TB) |
The number of disks in a RAID disk array |
ROPS (read operations per second) |
WOPS (write operations per second) |
RAID disk array size (TB) |
The number of disks in a RAID disk array |
||||||
1000 |
1 |
200 |
Not processed |
96 |
12 |
100 |
1000 |
1.9 |
4 |
300 |
300 |
Depends on the preferred storage policy |
4 |
2000 |
2 |
500 |
Not processed |
128 |
20 |
100 |
1000 |
2 |
4 |
500 |
500 |
4 |
|
5000 |
1 |
1000 |
Not processed |
160 |
36 |
100 |
1000 |
2 |
4 |
1000 |
600 |
4 |
|
10,000 |
2 |
1000 |
Not processed |
192 |
40 |
100 |
1000 |
2 |
4 |
2000 |
800 |
12 |
|
5000 |
5 |
Not processed |
2000 |
144 |
20 |
100 |
1000 |
1.9 |
4 |
1000 |
600 |
6 |
|
10,000 |
20 |
Not processed |
4000 |
192 |
36 |
100 |
1000 |
1.9 |
4 |
2000 |
800 |
12 |
|
15,000 |
20 |
Not processed |
4000 |
256 |
48 |
100 |
1000 |
1.9 |
4 |
2000 |
800 |
12 |
|
Example calculations of required server configuration for Kaspersky Anti Targeted Attack Platform components If you want to:
you need two servers with the following hardware:
The above calculation is also valid for an infrastructure with 5000 hosts with Kaspersky Endpoint Agent for Linux or a combination of components (for example, 9000 hosts with Kaspersky Endpoint Agent for Windows and 2000 hosts with Kaspersky Endpoint Agent for Linux). |
Disk space requirements on the server with the Central Node component
When no Sensor component is used on the server with the Central Node component, it is obligatory to have at least 2,000 GB of free space on the first disk subsystem and at least 2,400 GB on the second disk subsystem. The amount of space required on the second disk subsystem depends on the preferred storage policy and can be calculated using the following formula:
150 GB + <number of Kaspersky Endpoint Agent for Windows hosts>/15,000 * (400 GB + 240 GB * <number of days to store data>)
This formula can be used to roughly estimate the required disk space. The actual amount of stored data depends on the traffic profile of the organization and may differ from the calculated result.
The minimum free disk space requirements for each data type are presented in the table below.
Minimum requirements for disk space on the server with the Central Node component when no Sensor component is used
Data type |
First disk subsystem (GB) |
Second disk subsystem (GB) |
|---|---|---|
Targeted Attack Analyzer database |
0 |
1500 |
Database of detected objects |
50 |
0 |
Queues of detection technologies |
390 |
0 |
Task queue |
1 |
0 |
Data received after analysis by the Sandbox component |
300 |
0 |
Quarantine |
300 |
0 |
Files awaiting rescan |
300 |
0 |
Redis database dump file |
16 |
0 |
Operating system |
25 |
0 |
Temporary files |
64 |
0 |
Trace files |
50 |
100 |
Update packages |
1 |
0 |
Total |
1497 |
1600 |
When the Sensor component is used on the server with the Central Node component, it is obligatory to have at least 1900 GB of free space on the first disk subsystem and at least 3900 GB on the second disk subsystem. The minimum free disk space requirements for each data type are presented in the table below.
Minimum requirements for disk space on the server with the Central Node component when a Sensor component is used
Data type |
First disk subsystem on the server with the Central Node component (GB) |
Second disk subsystem on the server with the Central Node component (GB) |
Disk space on a server with the Sensor component (GB) |
|---|---|---|---|
Targeted Attack Analyzer database |
0 |
1500 |
0 |
Database of detected objects |
50 |
0 |
0 |
Queues of detection technologies |
390 |
0 |
0 |
Task queue |
1 |
0 |
0 |
Data received after analysis by the Sandbox component |
300 |
0 |
0 |
Quarantine |
300 |
0 |
0 |
Files awaiting rescan |
300 |
0 |
0 |
Redis database dump file |
16 |
0 |
16 |
Operating system |
25 |
0 |
25 |
Temporary files |
32 |
0 |
32 |
Trace files |
50 |
100 |
150 |
Update packages |
1 |
0 |
1 |
Total |
1465 |
1600 |
224 |
If you have configured integration with the external system using REST API, you must allocate additional resources required for processing objects of this system. Additional hardware requirements are presented in the table below.
Hardware requirements for the server with the Central Node component with integrated external systems
Maximum number of processed objects per second |
Number of additional logical cores |
The number of additional servers with the Sandbox component |
|---|---|---|
8 |
2 |
1 |
16 |
4 |
2 |
24 |
7 |
3 |
Requirements for the PCN server in distributed solution mode
If the load on the SCN servers is light, hardware requirements for the PCN server are the same as for a server with Central Node component in standalone mode.
Hardware requirements for the PCN server with 10 SCN servers under heavy load are listed in the table below.
Hardware requirements for the PCN server
Maximum number of Kaspersky Endpoint Agent for Windows hosts |
Maximum number of email messages per second |
Maximum volume of traffic from SPAN ports (Mbps) |
Minimum RAM (GB) |
Minimum number of logical cores |
First disk subsystem |
Second disk subsystem |
||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
ROPS (read operations per second) |
WOPS (write operations per second) |
RAID disk array size (TB) |
The number of disks in a RAID disk array |
ROPS (read operations per second) |
WOPS (write operations per second) |
RAID disk array size (TB) |
The number of disks in a RAID disk array |
|||||
10,000 |
0 |
0 |
160 |
24 |
100 |
1000 |
1 |
4 |
800 |
800 |
4 |
10 |
1000 |
1 |
200 |
112 |
40 |
100 |
1000 |
1.9 |
4 |
600 |
600 |
1.3 |
4 |
5000 |
5 |
2000 |
160 |
28 |
100 |
1000 |
1.9 |
4 |
300 |
300 |
2.5 |
6 |
10,000 |
20 |
4000 |
208 |
40 |
100 |
1000 |
1.9 |
4 |
1000 |
800 |
4 |
12 |
Communication channel requirements
The minimum requirements for the communication channel between computers with the Endpoint Agent component and the server with the Central Node component are presented in the table below.
Minimum requirements for the communication channel between computers with the Endpoint Agent component and the server with the Central Node component
Maximum number of Kaspersky Endpoint Agent for Windows hosts |
Required link bandwidth reserved for Endpoint Agent for Windows components (Mbps) |
|---|---|
10 |
1 |
50 |
2 |
100 |
3 |
1000 |
20 |
10,000 |
200 |
Minimum requirements for the communication channel between the PCN and SCN servers in distributed solution mode are listed in the table below.
Minimum requirements for the communication channel between the PCN and SCN servers
Maximum number of Kaspersky Endpoint Agent for Windows hosts |
Maximum number of email messages per second |
Maximum volume of traffic from SPAN ports (Mbps) |
Required communication channel bandwidth (Mbps) |
|---|---|---|---|
5000 |
5 |
2000 |
20 |
10,000 |
20 |
4000 |
30 |
Hardware requirements for Central Node cluster servers
A cluster must include at least 4 servers: 2 storage servers and 2 processing servers. To process traffic from 15,000 hosts with Kaspersky Endpoint Agent, you need at least 2 storage servers and 2 processing servers. To process traffic from 30,000 hosts with Kaspersky Endpoint Agent, you need at least 2 storage servers and 3 processing servers.
Each cluster server must have two network adapters to configure cluster and external subnet. The cluster subnet must operate at 10 Gbit/s. The external subnet must operate at 1 Gbit/s.
For a clustered subnet, the following requirements must also be met:
- A cluster subnet must include only the cluster servers and network switches.
- The cluster servers must all be in the same L1 or L2 segment. To do this, you can connect all the servers in the cluster to a single network switch or use software tunneling. For example, L2TPv3 or Overlay Transport Virtualization (OTV).
- The "network latency" value must meet the "single digit latency" requirement, that is, the value must be less than 10 milliseconds.
The hardware requirements for cluster servers when using KEDR functionality are listed in the table below.
Hardware requirements for processing servers when using KEDR functionality
Minimum RAM (GB) |
Minimum number of logical cores |
RAID disk array type |
The number of disks in a RAID disk array |
Single HDD volume (GB) |
|---|---|---|---|---|
256 |
48 |
RAID 1 |
2 |
1200 |
Hardware requirements for storage servers when using KEDR functionality
Minimum RAM (GB) |
Minimum number of logical cores |
First disk subsystem |
Second disk subsystem |
|||
|---|---|---|---|---|---|---|
RAID disk array type |
The number of disks in a RAID disk array |
Single HDD volume (GB) |
Number of disks |
Single HDD volume (GB) |
||
128 |
16 |
RAID 1 |
2 |
1200 |
6 |
1200 |
The performance requirements for disk subsystems are equivalent to those specified in the table Hardware requirements for a server with the Central Node component when using KEDR functionality (see above).
Calculations for the Sandbox component
The hardware requirements for a server with the Sandbox component depend on the type and volume of processed traffic and on the permissible object scan time.
By default, the permissible object scan time is 1 hour. To reduce this time, you need a more powerful server or more servers with the Sandbox component.
It is recommended to calculate the configuration of the Sandbox component as follows:
- Install the Central Node and Sensor components on one server and the Sandbox component on a different server for pilot operation of the program.
To receive sufficient statistical data, the program must process traffic of the organization for a week.
- Run the data recording script by executing the following commands:
kata-collect --output-dir path-to-folder--output-dir <path to directory>When the script finishes running, the collect.tar.gz archive will be moved to the specified directory.
- Forward this archive to Kaspersky Lab staff for analysis.
If multiple virtual machines are started simultaneously, the speed of processing objects from the queue is increased.
Hardware requirements for the server hosting the Sandbox component
The calculation of the number of servers with the Sandbox component depending on the load is shown in the table below.
Hardware requirements of the Sandbox component depending on the volume of processed traffic
Maximum number of email messages per second |
Maximum volume of traffic from SPAN ports (Mbps) |
Maximum number of Kaspersky Endpoint Agent for Windows computers |
Number of physical servers with the Sandbox component |
|
|---|---|---|---|---|
When using three |
When using three |
|||
1 |
200 |
1000 |
1 |
1 |
2 |
500 |
3000 |
1 |
1 |
1 |
1000 |
5000 |
1 |
1 |
5 |
2000 |
5000 |
1 |
1 |
20 |
4000 |
10000 |
2 |
3 |
The estimation of the number of Sandbox components is listed for servers with the following configuration:
- When installing the Sandbox component on a physical server:
- 2 Intel Xeon 8 Core (HT) CPUs
- 80 GB of RAM
- 2 HDDs, 300 GB each
- When installing the Sandbox component on a VMware ESXi virtual machine:
- Intel Xeon 15 Core (HT) processor at 2.1 GHz or higher
- 32 GB of RAM
- 300 GB HDD
On the virtual machine:
- Nested virtualization enabled.
- Latency Sensitivity option set to High.
- Entire RAM is reserved.
- Entire CPU frequency is reserved.
When installing the Sandbox component on a VMware ESXi virtual machine, you must set the limit for simultaneously running virtual machines to 12.
The performance of 3 or 4 virtual machines of the Sandbox component is identical to one Sandbox component on a physical server.