Common scenarios for deployment and installation of program components
The scenario for deployment and installation of program components is determined by the planned load on the program servers.
Kaspersky Endpoint Agent can be installed on any computers that belong to the organization's IT infrastructure and run the Windows operating system. Outbound connections from computers with Kaspersky Endpoint Agent to the server hosting the Central Node component must be allowed directly, without a proxy server.
You can install one or multiple Central Node components. If you install multiple Central Node components, you can use them independently of each other or combine them for centralized management in distributed solution mode.
The deployment scenario selection depends on the utilized program functionality. All scenarios listed in this manual also apply to the deployment of the program on a virtual platform.
Full functionality (KATA and KEDR)
When using KATA and KEDR functionality, you can scan network traffic, mail traffic, and data on corporate LAN computers.
If more than 5000 Kaspersky Endpoint Agent programs are installed within the organization, it is not recommended to use the Central Node component to process traffic.
You can use the Sensor component as a proxy server for connecting hosts to Kaspersky Endpoint Agent and the Central Node. One Sensor component supports the connection of up to 1000 Kaspersky Endpoint Agent hosts.
The criteria for selecting a deployment scenario when using KATA and KEDR functionality are presented in the table below. The selection algorithm is as follows:
- In each row of the table, select the cell containing the value of the criterion corresponding to your IT infrastructure.
If a row contains two cells with identical values, you must select the cell on the left.
- Select the right-most column in which there are marked cells.
Selecting a deployment scenario when using KATA and KEDR functionality
Criterion
Two-server scenario
Three-server scenario
Four- or more server scenario
Network traffic and mail traffic cannot be received on the same device.
No
Yes
Yes
Yes
Number of Kaspersky Endpoint Agent hosts
No
From 5000 to 10,000
From 5000 to 10,000
Over 10,000
1 Gbps
From 1 to 2 Gbps
Over 2 Gbps
Over 2 Gbps
The number of remote infrastructures in which traffic needs to be analyzed.
No
One
Two or more
Two or more
The capacities of one Sandbox component are insufficient to analyze all objects within acceptable time frames.
No
No
Yes
Yes
In distributed solution mode each program component must meet the hardware requirements specified in the sizing calculator.
Processing of network traffic, mail traffic, and web traffic (KATA)
It is recommended to use KATA functionality if the organization does not need to process data on corporate LAN computers. If this is the case, only network traffic and mail traffic are processed.
The criteria for selecting a deployment scenario when using KATA functionality are presented in the table below. The selection algorithm is as follows:
- In each row of the table, select the cell containing the value of the criterion corresponding to your IT infrastructure.
If a row contains two cells with identical values, you must select the cell on the left.
- Select the right-most column in which there are marked cells.
Selecting a deployment scenario when using KATA functionality
Criterion
Two-server scenario
Three-server scenario
Four- or more server scenario
Network traffic and mail traffic cannot be received on the same device.
No
Yes
Yes
1 Gbps
From 1 to 2 Gbps
Over 2 Gbps
The number of remote infrastructures in which traffic needs to be analyzed.
No
One
Two or more
The capacities of one Sandbox component are insufficient to analyze all objects within acceptable time frames.
No
No
Yes
Processing of data from corporate LAN computers (KEDR)
It is recommended to use KEDR functionality if the organization does not need to process traffic. If this is the case, only data on corporate LAN computers is processed.
Depending on the presence of a third-party Sandbox solution within the organization, you can use one of the following deployment scenarios:
- Without a Sandbox component
- With a Sandbox component
Two-server deployment scenario.
When using KATA and KEDR functionality, you can install the Kaspersky Endpoint Agent program on corporate LAN computers. When using KATA functionality, the Kaspersky Endpoint Agent program is not installed.
When using this deployment scenario, the Central Node and Sensor components are installed on the same server or cluster. This server or cluster receives traffic, performs an initial analysis of traffic and a deeper analysis of extracted files. Based on the scan results, components detect signs of targeted attacks on the organization's IT infrastructure.
The Sandbox component is installed on the other server.
The scenario for program operation when deployed on two servers is presented in the figure below.
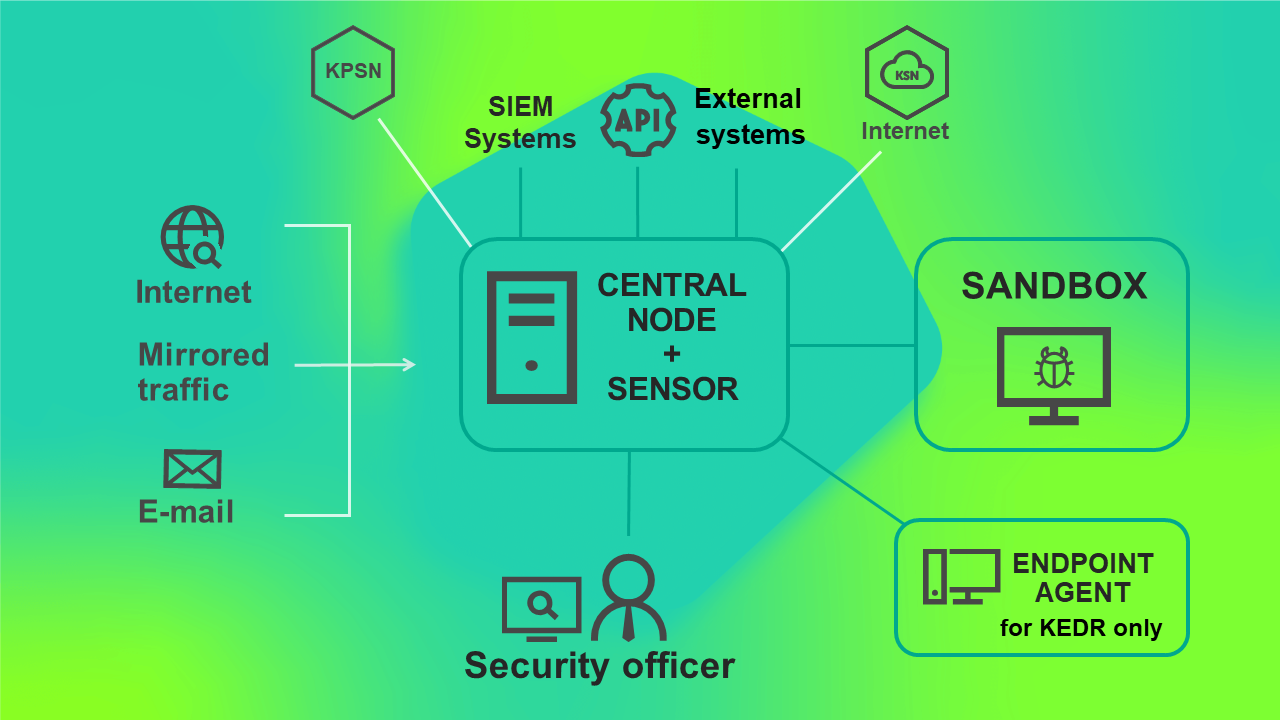
Program operating scenario when deployed on two servers
Three-server deployment scenario.
When using KATA and KEDR functionality, you can install the Kaspersky Endpoint Agent program on corporate LAN computers. When using KATA functionality, the Kaspersky Endpoint Agent program is not installed.
When using this deployment scenario, the Sensor, Central Node and Sandbox components are installed on separate servers. The Central Node component can also be deployed as a cluster. The server with the Sensor component receives traffic, performs an initial analysis, extracts files and forwards them to the Central Node component for a deeper analysis.
Using this deployment scenario, the Central Node component can receive traffic and perform an initial analysis of data in the main infrastructure. In this case, you can install the Sensor component on a server of a remote infrastructure whose traffic needs to be analyzed. If the channel bandwidth in the main infrastructure is more than 2 Gbps, you are advised to install the server with the Sensor component in the main infrastructure.
The traffic exchanged between the Central Node and Sensor components comprises up to 20% of traffic received by the Sensor component.
The program operating scenario when deployed on three servers is presented in the figure below.
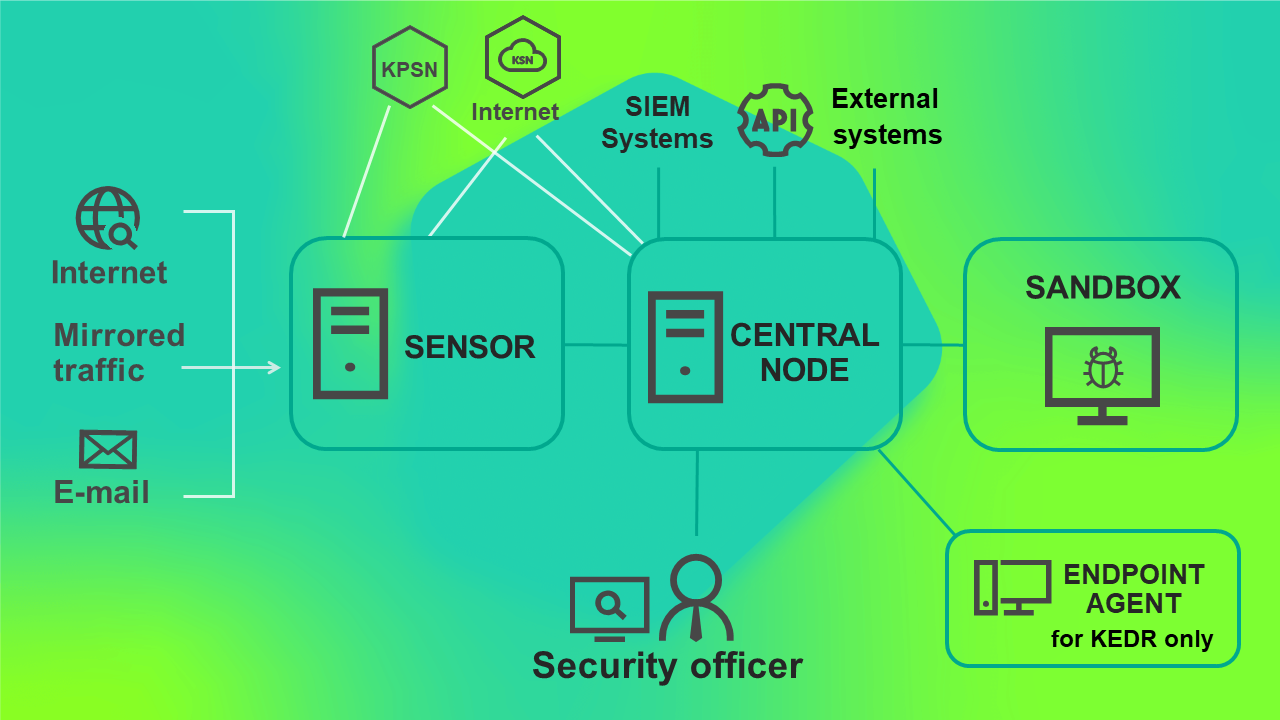
Program operating scenario when deployed on three servers
Scenario of deployment on four or more servers.
When using KATA and KEDR functionality, you can install the Kaspersky Endpoint Agent program on corporate LAN computers. When using KATA functionality, the Kaspersky Endpoint Agent program is not installed.
If there is a large volume of traffic, you can install multiple Sensor components or multiple Sandbox components on different servers. This scenario is recommended for deployment in large organizations.
You can also use one Sandbox component to connect to multiple Central Node components.
The operating schematic of the program when deployed on four or more servers is presented in the figure below.
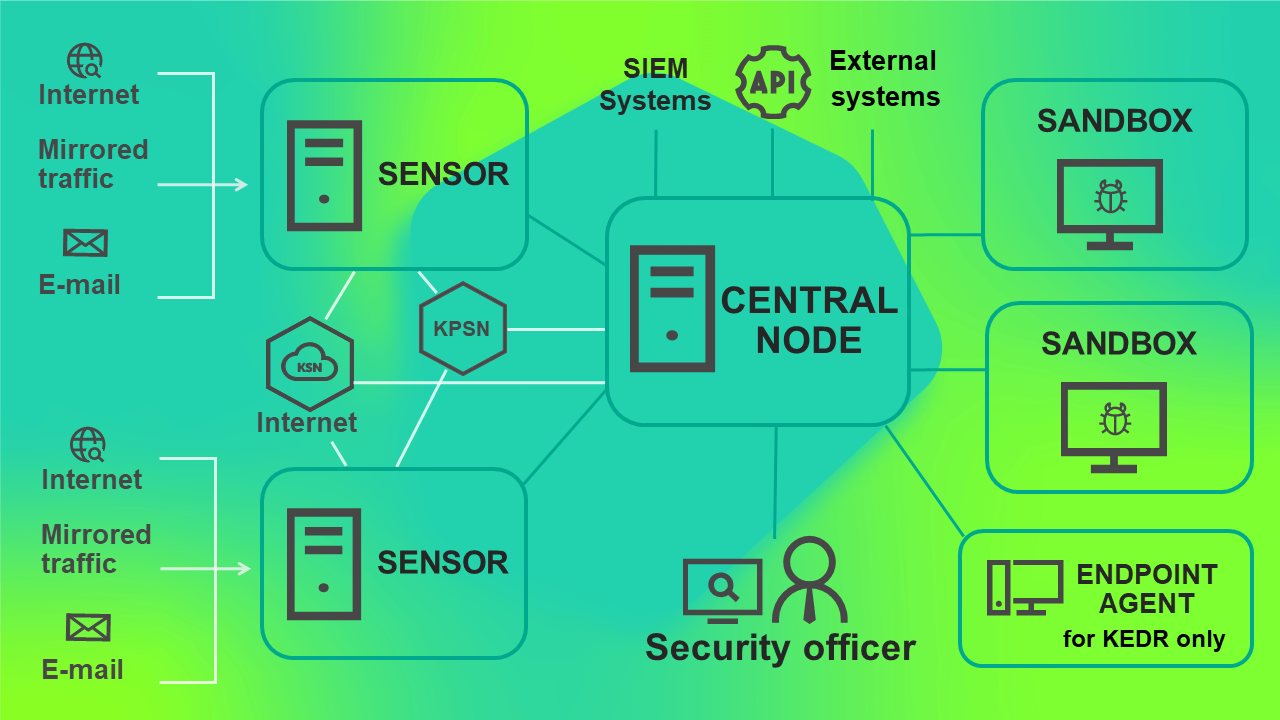
Program operating scenario when deployed on four or more servers
Scenario for deploying KEDR functionality with a Sandbox component.
Using this deployment scenario, you need to install the Central Node component separately from the Sensor component.
The program operating scenario when deploying KEDR functionality with the Sandbox component is presented in the figure below.
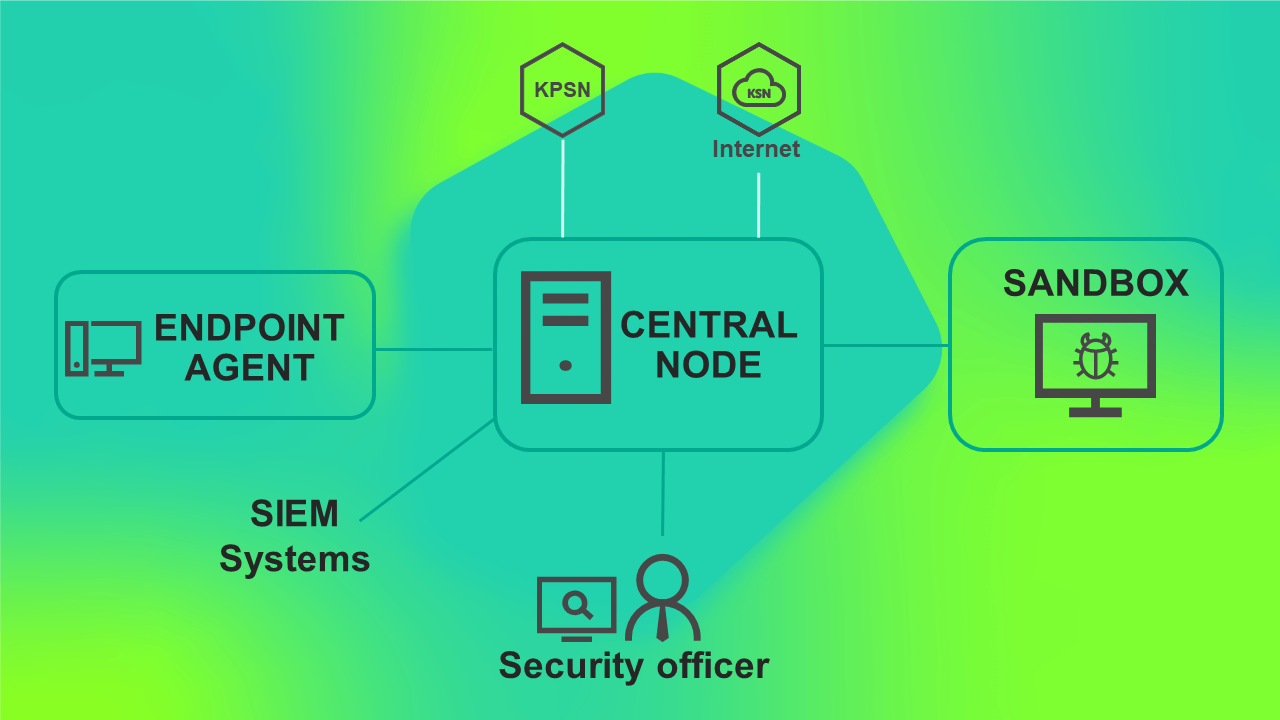
Program operating scenario when deploying KEDR functionality with the Sandbox component
Scenario for deploying KEDR functionality without a Sandbox component.
You do not need to install the Sandbox component and can use the Central Node component only for managing the Kaspersky Endpoint Agent program and data analysis.
Using this deployment scenario, you need to install the Central Node component separately from the Sensor component.
The program operating scenario when deploying KEDR functionality without the Sandbox component is presented in the figure below.
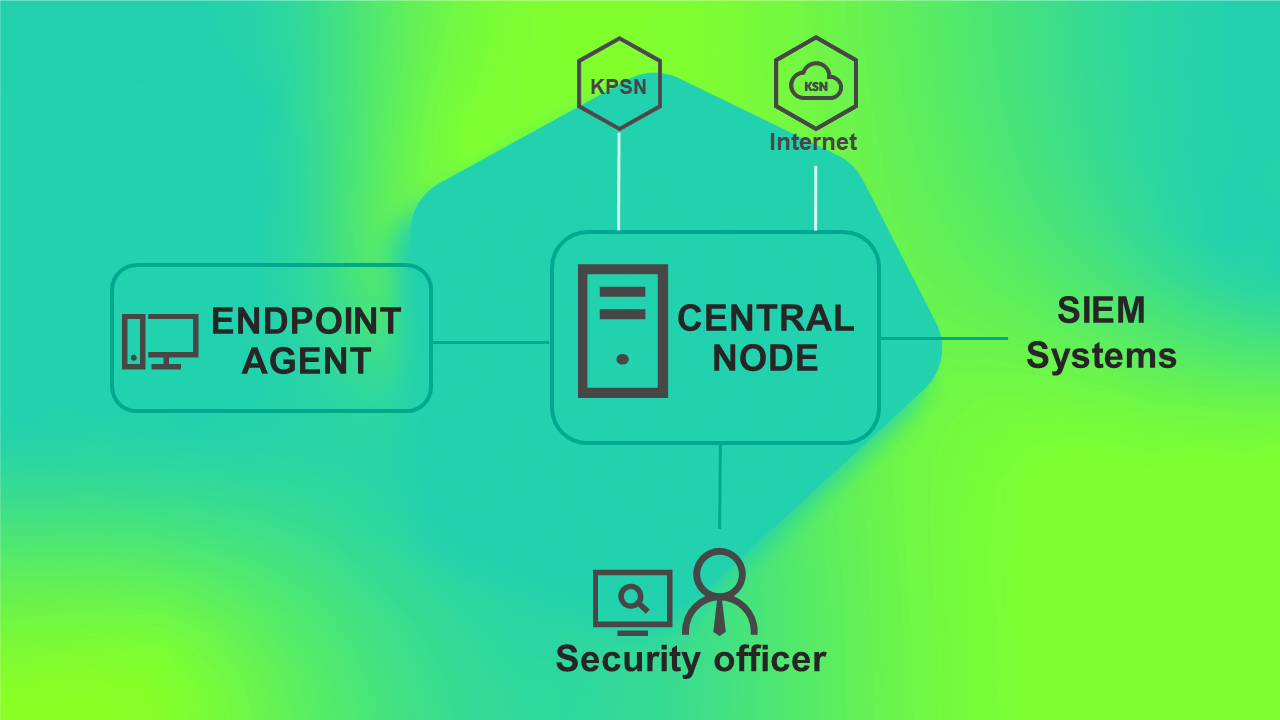
Program operating scenario when deploying KEDR functionality without the Sandbox component