Contents
- Managing the application via Kaspersky Security Center
Managing the application via Kaspersky Security Center
Kaspersky Security for Virtualization 6.0 Agentless is controlled via Kaspersky Security Center, a centralized system that enables remote administration of Kaspersky applications. In the case of Kaspersky Security for Virtualization 6.0 Agentless, a client device of Kaspersky Security Center is an SVM. Protected virtual machines are not considered client devices from the perspective of Kaspersky Security Center because the Kaspersky Security Center Network Agent is not installed on them.
After Kaspersky Security has been installed in the virtual infrastructure, SVMs send their details to Kaspersky Security Center. Based on this information, Kaspersky Security Center combines SVMs into KSC clusters (Kaspersky Security Center clusters):
- The "VMware vCenter Agentless" cluster is a KSC cluster that corresponds to the standalone VMware vCenter Server. This cluster contains all SVMs deployed on VMware ESXi hypervisors managed by one standalone VMware vCenter Server.
The KSC cluster corresponding to the VMware vCenter Server is assigned the name
VMware vCenter '<name>' (<IP address or domain name>) Agentless, where:- <name> is the name of the VMware vCenter Server corresponding to this KSC cluster. If the name of the VMware vCenter Server is not defined or matches its IP address, the name is omitted.
- <IP address or domain name> is the IP address or domain name of the VMware vCenter Server corresponding to this KSC cluster.
Virtual machines that are managed by this VMware vCenter Server form the protected infrastructure of the "VMware vCenter Agentless" cluster.
- A VMware vCloud Director Agentless cluster is a KSC cluster corresponding to the VMware vCloud Director server. This cluster contains all SVMs deployed on VMware ESXi hypervisors under all VMware vCenter Servers connected to one VMware vCloud Director.
The name
VMware vCloud Director (<IP address or domain name>) Agentlessis assigned to the KSC cluster corresponding to the VMware vCloud Director server (<IP address or domain name> refers to the IP address or domain name of the VMware vCloud Director corresponding to this KSC cluster).Virtual machines that are managed by VMware vCenter Servers connected to this VMware vCloud Director Server, including virtual machines within vCloud Director organizations, form the protected infrastructure of the "VMware vCloud Director Agentless" cluster corresponding to the VMware vCloud Director.
Kaspersky Security Center creates a separate administration group for each KSC cluster in the Managed devices folder of the Administration Console and assigns the name of the KSC cluster to this group. When an administration group with the name of a KSC cluster is selected in the console tree, the Devices tab in the workspace displays a list of SVMs belonging to this KSC cluster.
You can open the cluster properties window by selecting the Clusters and server arrays subfolder within the folder of the administration group named after the KSC cluster. In the properties window of the KSC cluster, you can view the following:
- List of SVMs within this KSC cluster (Nodes section)
- List of virtual machines within the protected infrastructure of this KSC cluster
- List of tasks created for SVMs of this KSC cluster
Kaspersky Security is managed through Kaspersky Security Center by using policies and tasks:
- A policy is a set of application settings that are defined for an administration group. For Kaspersky Security, a policy is applied on SVMs and determines the settings used by SVMs to protect virtual machines that are within the scope of the policy.
Each policy contains one or multiple protection profiles. Protection profiles let you configure the settings for file protection of virtual machines.
- Tasks are performed on SVMs and they implement application functions such as application activation, scanning of virtual machines, updating application databases, and automatic installation of patches for the application.
For more detailed information about policies and tasks, please refer to the Kaspersky Security Center documentation.
About Kaspersky Security policies
When configuring virtual infrastructure protection, it is recommended to account for the specific features of Kaspersky Security policies.
The policy scope, which is a set of virtual machines for which a policy can be used for protection, depends on the type of policy and the protected infrastructure that was selected during configuration of the policy and policy scope (set of SVMs on which the policy is applied).
Kaspersky Security policy types
The following types of policies are provided for Kaspersky Security:
- Main policy. This policy lets you configure the settings for virtual machine file threat protection using protection profiles, network threat protection settings, and the following application settings:
- Settings of notifications about events in application operation.
- Backup settings.
- Kaspersky Security Network usage settings.
- SNMP monitoring settings.
If the application is operating in multitenancy mode, the main policy determines the Network Threat Protection settings for all virtual machines and the File Threat Protection settings for virtual machines that are not part of vCloud Director organizations.
It is recommended to create main policies on the main Administration Server of Kaspersky Security Center. Main policies are created using the Kaspersky Security main administration plug-in.
- Tenant policy (used only if the application is operating in multitenancy mode). This policy lets you configure the settings of protection for virtual machines that are part of vCloud Director organizations. You can use this policy to define the following settings:
- Settings of notifications about events that occur when protecting and scanning virtual machines of a tenant (only in a policy that was created on the main Administration Server of Kaspersky Security Center).
- Individual file protection settings for virtual machines of the tenant.
- KSN usage settings for the tenant organization.
You can create tenant policies on the main Administration Server or on virtual Administration Servers of Kaspersky Security Center by using the Kaspersky Security administration plug-in for tenants.
Protected infrastructure of a policy
Depending on the protected infrastructure that you select when configuring a policy, the following policies are distinguished as follows:
- Policy for one VMware vCenter Server – lets you configure the settings for protecting a virtual infrastructure managed by one VMware vCenter Server.
- Policy for the entire protected infrastructure – lets you configure the settings for protecting a virtual infrastructure managed by all VMware vCenter Servers to which the Integration Server connects.
Policy application scope
In Kaspersky Security, a policy is applied on SVMs. Each SVM can protect only the virtual machines running on the same hypervisor where the SVM is deployed. Therefore, the policy protection scope (set of virtual machines for which a policy can be used for protection) depends on the policy application scope (set of SVMs on which the policy is applied).
The policy application scope is determined by the location of the policy within the hierarchy of Kaspersky Security Center administration groups. A policy is applied on SVMs as follows:
- The main policy in an administration group containing a KSC cluster is applied on all SVMs of this KSC cluster.
- The main policy in an administration group or folder that is the parent in relation to the groups containing KSC clusters is applied on all SVMs of child KSC clusters.
- The tenant policy on a virtual Administration Server created in the group of the "VMware vCloud Director Agentless" cluster corresponding to the VMware vCloud Director is applied on all SVMs of this KSC cluster.
Inheriting policy settings
According to the order of inheritance of Kaspersky Security Center policies, by default the settings of policies are transferred to policies of nested administration groups and subordinate Administration Servers (for more details, please refer to the Kaspersky Security Center documentation). The settings and settings groups of policies have a "lock" attribute, that shows whether or not you are allowed to change these settings in nested policies. If a setting or a group of settings in a policy is "locked" ( ), the values of these settings are defined in nested policies and cannot be redefined.
), the values of these settings are defined in nested policies and cannot be redefined.
About Kaspersky Security protection profiles
The following protection profiles are provided in Kaspersky Security policies:
- The main protection profile is automatically created when a policy is created. Although the main protection profile cannot be deleted, you can edit its settings.
- You can create additional protection profiles after creating a policy. Additional protection profiles let you flexibly configure different protection settings for different virtual machines within the protected infrastructure. A policy can contain multiple additional protection profiles.
You can configure the following File Threat Protection settings in protection profiles:
- Security level. You can select one of the preset security levels (High, Recommended, Low) or configure your own security level (Custom). The security level defines the following scan settings:
- Scanning of archives, self-unpacking archives, embedded OLE objects, and compound files
- Restriction on file scan duration
- List of objects to detect
- Action that Kaspersky Security performs after detecting infected files.
- Protection scope (scanning of network drives during protection of virtual machines).
- Exclusions from protection (by name, by file extension or full path, by file mask or path to the folder containing files to be skipped).
A protection profile can be assigned to an individual VMware virtual infrastructure object or to the root element of the protected infrastructure, which can include an Integration Server, for example (see the figure below).
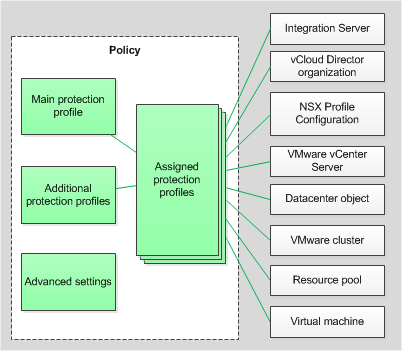
Protection profiles
By default, a protection profile assigned to the root element of a protected infrastructure is inherited by all child elements of the protected infrastructure (for example, by all VMware vCenter Servers to which the Integration Server connects). Protection profiles are also inherited according to the hierarchy of VMware virtual infrastructure objects: by default, the protection profile assigned to a virtual infrastructure object is inherited by all of its child objects, including by virtual machines. You can either assign a specific protection profile to a virtual machine, or let it inherit the protection profile that is used by its parent object.
In the main policy, which determines the protection settings for a virtual infrastructure managed by one VMware vCenter Server, you can directly assign protection profiles to virtual infrastructure objects or use NSX Profile Configurations to assign file protection settings.
Only one protection profile may be assigned to a single virtual infrastructure object. Kaspersky Security protects virtual machines according to the settings that are specified in the protection profile assigned to these virtual machines.
Virtual infrastructure objects that have no assigned protection profile are excluded from protection.
If you exclude a virtual infrastructure object from protection, all child objects are also excluded from protection by default. You can indicate whether or not to exclude child objects that have been assigned their own protection profile.
Protection profile inheritance makes it possible to simultaneously assign identical protection settings to multiple virtual machines or exclude them from protection. For example, you can assign identical protection profiles to the virtual machines within a VMware cluster or resource pool.
Page topAbout managing policies
Policies are created by using the Wizard, which is started by clicking the New policy button located in the workspace of the folder or administration group on the Policies tab.
In a folder or administration group, you can create multiple policies but only one of them can be active. When you create a new active policy, the previous active policy becomes inactive.
You can change the settings of a policy after its creation in the policy properties window.
To open the policy properties window:
- In the Kaspersky Security Center Administration Console, select the folder or administration group in which the policy was created.
- In the workspace, select the Policies tab.
- In the list of policies, select the policy and open the Properties: <Policy name> window by double-clicking on the policy or by selecting Properties in the context menu.
You can also perform the following actions with policies:
- Copy policies from one folder or administration group into another.
- Export policies to a file and import policies from a file.
- Convert policies of the previous version of the application.
- Delete policies.
For more information about managing policies, see Kaspersky Security Center documentation.
Page topSpecial considerations when using Kaspersky Security policies
Main policy in the Managed devices folder of the main Administration Server
This policy is automatically created using the Quick Start Wizard for the managed application after installing the Kaspersky Security main administration plug-in. You can also create such policy manually using the Policy Wizard.
The policy is applied on all SVMs of all KSC clusters.
The entire protected infrastructure must be selected as the protected infrastructure for this policy. The Integration Server serves as the root element of the protected infrastructure.
The scope of this policy includes the following virtual machines:
- File protection applies to all virtual machines within the protected infrastructure of the policy, except for virtual machines that are part of vCloud Director organizations.
- Network protection applies to all virtual machines within the protected infrastructure of the policy (including virtual machines that are part of vCloud Director organizations).
File protection and network protection are disabled by default.
To enable file protection, you need to assign protection profiles to objects of the protected infrastructure in policy properties. You can assign the automatically created main protection profile or create and assign additional protection profiles.
Please keep in mind that the settings of the main policy located in the Managed devices folder are inherited by the main policies located in all nested administration groups. Settings that are closed with a "lock" cannot be redefined in nested policies.
To enable network protection, you need to configure the settings for Intrusion Prevention and Web Addresses Scan in policy properties.
Main policy in the group that contains the "VMware vCenter Agentless" cluster
You can create this policy manually by using the New Policy Wizard. The policy is applied on all SVMs of this "VMware vCenter Agentless" cluster.
You must select one VMware vCenter Server as the protected infrastructure for this policy and indicate the VMware vCenter Server corresponding to the "VMware vCenter Agentless" cluster. The root element of the protected infrastructure is the indicated VMware vCenter Server.
The scope of this policy includes all virtual machines within the protected infrastructure of this "VMware vCenter Agentless" cluster.
File protection is enabled by default: the main protection profile is assigned to the VMware vCenter Server and is inherited by all child objects of the virtual infrastructure. If you want to configure different file protection settings for different virtual machines within the protected infrastructure of this KSC cluster, you need to create and assign additional protection profiles in the policy properties.
Network protection is disabled by default. To enable network protection, you need to configure the settings for Intrusion Prevention and Web Addresses Scan in policy properties.
Main policy in the group that contains the "VMware vCloud Director Agentless" cluster
You can create this policy manually by using the New Policy Wizard. The policy is applied on all SVMs of this "VMware vCloud Director Agentless" cluster.
The entire protected infrastructure must be selected as the protected infrastructure for this policy. The Integration Server serves as the root element of the protected infrastructure.
The scope of this policy includes the following virtual machines:
- File protection applies to all virtual machines within the protected infrastructure of the "VMware vCloud Director Agentless" cluster that are not part of vCloud Director organizations.
- Network protection applies to all virtual machines within the protected infrastructure of the "VMware vCloud Director Agentless" cluster, including virtual machines that are part of vCloud Director organizations.
File protection and network protection are disabled by default.
To enable file protection, you need to assign protection profiles to objects of the protected infrastructure in policy properties. You can assign the automatically created main protection profile or create and assign additional protection profiles.
In the properties of the main policy for the "VMware vCloud Director Agentless" cluster, you can assign protection profiles to any objects of the protected infrastructure. However, file protection settings will be applied only for protecting virtual machines that are not part of vCloud Director organizations and that are managed by VMware vCenter Servers connected to VMware vCloud Director mapped to the "VMware vCloud Director Agentless" cluster.
To enable network protection, you need to configure the settings for Intrusion Prevention and Web Addresses Scan in policy properties.
Tenant policy in the Managed devices folder of the main Administration Server
This policy is automatically created using the Quick Start Wizard for the managed application after installing the Kaspersky Security administration plug-in for tenants on the main Administration Server. You can also create such policy manually using the Policy Wizard.
If the Managed devices folder of the main Administration Server is missing a tenant policy, Kaspersky Security Center does not register events that occur when scanning and protecting virtual machines of tenants, and does not display virtual machines of tenants within the KSC cluster protected infrastructure or in the list of virtual machines protected by SVMs.
The settings of this policy are not used directly for the protection of virtual machines: the protected infrastructure is not selected for this policy. However, the settings of the main protection profile and KSN usage settings configured in this policy may be inherited in tenant policies located in nested administration groups, for example, in the Managed devices folder of the virtual Administration Server. This way, you can define the same file protection settings for the virtual infrastructures of all tenants.
In this policy, you can configure the settings for notifications about events that occur when protecting and scanning virtual machines of tenants.
Please keep in mind that the settings that are closed with a "lock" in a tenant policy on the main Administration Server will be unavailable for editing on virtual Administration Servers. The administrators of tenants will not be able to configure these settings.
If you want to centrally enable the use of Kaspersky Security Network for protection of all virtual machines of tenants, you need to first obtain the consent of tenants to send KSN usage information and other information to Kaspersky depending on the KSN usage mode that you selected (standard KSN or extended KSN).
Tenant policy in the group that contains the "VMware vCloud Director Agentless" cluster
This policy is equivalent to a tenant policy in the Managed devices folder of the main Administration Server (see above). You can create this policy manually by using the New Policy Wizard.
Tenant policy in the Managed devices folder of the virtual Administration Server
You can create this policy manually by using the New Policy Wizard.
The policy is applied on all SVMs of the "VMware vCloud Director Agentless" cluster corresponding to the VMware vCloud Director mapped to the vCloud Director organization containing the virtual machines of the tenant.
The protected infrastructure for this policy is selected automatically. The root element is the "vCloud Director organization" that combines all virtual Datacenters of the tenant.
The scope of this policy includes all virtual machines within the vCloud Director organization that corresponds to this virtual Administration Server.
File protection is enabled by default: the main protection profile is assigned to the root element "vCloud Director organization" and is inherited by all objects of the virtual infrastructure of the tenant. If you want to configure different file protection settings for different virtual machines within the virtual infrastructure of the tenant, you need to create and assign additional protection profiles in the policy properties.
Page topAbout Kaspersky Security tasks
It is recommended to use the following types of tasks for managing Kaspersky Security through Kaspersky Security Center:
- Group task – a task that is performed on the client devices of the selected administration group. For Kaspersky Security, group tasks can be run on SVMs of one KSC cluster or on all SVMs.
- Global task. A task for one or more SVMs regardless of whether or not they are included in an administration group.
For more information about managing tasks, see Kaspersky Security Center manuals.
The following tasks are available for Kaspersky Security:
- Full and Custom Scan tasks, which let you scan all or just the specified virtual machines within the task scope.
- Service tasks, which let you activate the application, update the application databases, roll back updates, and install application patches.
Full Scan task
The Full Scan task lets you run a virus scan on the files of all virtual machines within the task scope. The scope of a task depends on where the task is located within the hierarchy of administration groups of Kaspersky Security Center, and depends on the Kaspersky Security administration plug-in that you use to create the task.
You can create Full Scan tasks by using one of the Kaspersky Security administration plug-ins:
- Main administration plug-in – to scan virtual machines that are not part of a vCloud Director organization.
- Administration plug-in for tenants – to scan virtual machines that are part of a vCloud Director organization, which means to scan virtual machines of tenants.
Full Scan task created using the main administration plug-in
If you are creating a Full Scan task using the Kaspersky Security main administration plug-in, the task scope is determined as follows:
- This task in the Managed devices folder of the main Administration Server of Kaspersky Security Center lets you scan all virtual machines within the entire protected infrastructure that are not part of a vCloud Director organization.
- This task in a group that contains a KSC cluster lets you scan all virtual machines within the protected infrastructure of this KSC cluster that are not part of a vCloud Director organization.
- The task in the Tasks folder configured for one or more SVMs lets you scan all virtual machines that are protected by the specified SVMs but that are not part of a vCloud Director organization.
An SVM can scan only the virtual machines running on the same hypervisor where the SVM is deployed.
Full Scan task created using the administration plug-in for tenants
Creation of a Full Scan task for virtual machines of tenants is supported only on a virtual Administration Server of Kaspersky Security Center. You can create a Full Scan task using the Kaspersky Security administration plug-in for tenants in the Managed devices folder of the virtual Administration Server. The scope of this task includes all virtual machines within the vCloud Director organization that corresponds to this virtual Administration Server.
Page topCustom Scan task
The Custom Scan task lets you run a virus scan on files of specified virtual machines from the task scope. The scope of a task depends on where the task is located within the hierarchy of administration groups of Kaspersky Security Center, and depends on the Kaspersky Security administration plug-in that you use to create the task.
You can create Custom Scan tasks by using one of the Kaspersky Security administration plug-ins:
- Main administration plug-in – to scan virtual machines that are not part of a vCloud Director organization.
- Administration plug-in for tenants – to scan virtual machines that are part of a vCloud Director organization, which means to scan virtual machines of tenants.
Custom Scan task created using the main administration plug-in
A Custom Scan task created using the main administration plug-in lets you scan virtual machines that are managed by one VMware vCenter Server and are not part of a vCloud Director organization.
It is recommended to create Custom Scan tasks by using the main administration plug-in in the following administration groups:
- If you want to scan virtual machines that are managed by a standalone VMware vCenter Server, you need to create a task in the group that contains the VMware vCenter Agentless cluster corresponding to this VMware vCenter Server and indicate this VMware vCenter Server as the task scope.
- If you want to scan virtual machines managed by a VMware vCenter Server connected to VMware vCloud Director, you need to create a task in the group that contains the "VMware vCloud Director Agentless" cluster corresponding to VMware vCloud Director, and indicate the necessary VMware vCenter Server as the task scope. You need to create a separate Custom Scan task for each VMware vCenter Server connected to VMware vCloud Director.
In the selected scope, you need to indicate the virtual machines that need to be scanned. You can specify individual virtual machines, VMware virtual infrastructure objects of a higher level of the hierarchy, or NSX Security Groups that include the relevant virtual machines.
Due to the specifics of configuring the scope of a Custom Scan task, it is recommended to create a Custom Scan task only in the specified administration groups, which means group tasks. If a Custom Scan task is configured for one or more SVMs (meaning a local or global task), correct configuration of the task scope cannot be guaranteed.
Custom Scan task created using the administration plug-in for tenants
Creation of a Custom Scan task for virtual machines of tenants is supported only on a virtual Administration Server of Kaspersky Security Center. You can create a Custom Scan task using the Kaspersky Security administration plug-in for tenants in the Managed devices folder of the virtual Administration Server. The scope of this task includes all virtual machines within the vCloud Director organization that corresponds to this virtual Administration Server. In this scope, you need to indicate the virtual machines that need to be scanned. You can specify individual virtual machines or VMware virtual infrastructure objects of a higher level of the hierarchy.
Page topService tasks
You can use the following service tasks to manage the application:
- Update. This task installs updates for application databases on the SVMs on which the task is run.
- Rollback. This task rolls back the last update of application databases on the SVMs on which the task is run.
- Application activation. As a result of this task, a license key for activating the application or for renewing the license term is added to SVMs on which the task is run.
- Automatic installation of patches. This task installs application patches on the SVMs on which the task is run.
You can create service tasks using the Kaspersky Security main administration plug-in on the main Administration Server.
The set of SVMs on which service tasks are run depends on the task's location within the hierarchy of Kaspersky Security Center administration groups:
- A task in the Managed devices folder is run on all SVMs.
- A task in a group that contains a KSC cluster is run on all SVMs of one KSC cluster.
- A task in the Tasks folder configured for one or more SVMs is run on the specified SVMs.
About task management
Tasks are created by using the Wizard, which is started by clicking the New task button located in the workspace of the folder or administration group on the Tasks tab.
You can change the settings of a task after its creation in the task properties window.
To open the task properties window:
- In the Kaspersky Security Center Administration Console, select the folder or administration group in which the task was created.
- In the workspace, select the Tasks tab.
- In the list of tasks, select the task and open the Properties: <Task name> window by double-clicking on the task or by selecting Properties in the context menu.
Regardless of the selected task run mode, you can start or stop the task at any time.
To start or stop a task:
- In the Kaspersky Security Center Administration Console, select the folder or administration group in which the task was created.
- In the workspace, select the Tasks tab.
- In the list of tasks, select the task that you want to start or stop.
- Click the Start or Stop button. The buttons are located to the right of the task list.
Information about the progress and results of the task can be viewed in the Kaspersky Security Center Administration Console in one of the following ways:
- In the Task results window. To open the window, click the View results link on the right of the task list displayed in the Tasks folder of the Kaspersky Security Center console tree or on the Tasks tab in the workspace of the folder or administration group.
- In the list of events that SVMs send to the Kaspersky Security Center Administration Server. The event list is displayed on the Events tab in the workspace of the Administration Server node.
You can also perform the following actions with tasks:
- Copy tasks from one folder or administration group into another.
- Export tasks to a file and import tasks from a file.
- Convert tasks from the previous version of the application.
- Delete tasks.
For more information about managing tasks, see Kaspersky Security Center documentation.
Page topAbout access rights to the settings of policies and tasks
The rights to access the settings of policies and tasks (read, write, execute) are defined for each user who has access to the Kaspersky Security Center Administration Server. In the Kaspersky Security Center Administration Console, you can grant user accounts the rights to perform certain actions within functional scopes of Kaspersky Security.
Kaspersky Security has the following functional scopes:
- Anti-Virus protection. This functional scope includes the following settings and functions:
- Enables or disables the anti-virus protection function.
- All security level settings in policies:
- Scan archives, self-extracting archives and embedded OLE objects.
- Scan large compound files.
- File scan duration limit.
- List of objects to detect.
- Action that Kaspersky Security performs when it detects infected files during virtual machine protection.
- Scan files on network drives during virtual machine protection.
- Enabling and disabling the web address scanning function.
- List of web address categories detected by Kaspersky Security.
- Action that Kaspersky Security performs if it detects a web address that belongs to one or more of the web address categories selected for detection.
- Backup settings.
- KSN usage settings.
- List of additional protection profiles in a policy.
- Assigning or changing the protected infrastructure for a policy.
- Assigning protection profiles to VMware virtual infrastructure objects.
- Full scan tasks and custom scan tasks.
- Basic functionality. This functional scope includes the following settings and functions:
- SNMP monitoring settings.
- Language of the blocked web address notification that is displayed in the browser on the protected virtual machine.
- Application database update task and latest application database update rollback task.
- Application activation task.
- Automatic patch installation task.
- Intrusion Prevention. This functional scope includes the following settings and functions:
- Enabling and disabling the Network Attack Blocker feature.
- Action that Kaspersky Security performs when it detects a network attack.
- Enabling and disabling Network Activity Scanner for virtual machines.
- Action that Kaspersky Security performs when it detects suspicious network activity.
- List of application categories whose signs of network activity are detected by Kaspersky Security.
- Duration for blocking the IP address from which the network attack or suspicious network activity originated.
- Trusted zone. This functional scope includes the following settings and functions:
- List of file extensions excluded from protection.
- List of file extensions included in the protection scope.
- List of folders and files excluded from protection.
- List of rules for identifying suspicious network activity that Kaspersky Security does not apply when analyzing traffic of protected virtual machines.
- List of network threat protection exclusion rules.
- List of web addresses that Kaspersky Security does not block, regardless of the configured web address scan settings.
The following actions are available to the user regardless of the rights of the user account within the functional scopes of Kaspersky Security:
- Viewing the settings of policies and tasks.
- Creating a policy.
Rights within the functional scopes of Kaspersky Security are required for performing the following actions with policies and tasks:
- To reconfigure a previously saved policy, the user account must have modification rights within the functional scopes of those settings.
- To modify the status of a policy (active / inactive) or remove a policy, the user account must have modification rights within the functional scopes of all policy settings. If a user account does not have the rights to edit any policy setting, the user cannot remove the policy or change the status of the policy.
- To create, remove, or configure the settings of tasks, the user account must have modification rights within the functional scope of the task.
- To run a task, the user account must have execution rights within the functional scope of the task.
Access to functional scopes of Kaspersky Security is configured in the properties window of the Kaspersky Security Center Administration Server in the Security section.
By default, the Security section is not displayed in the Administration Server properties window. To enable the display of the Security section, you must select the Display security settings sections check box in the Configure interface window (View → Configure interface menu) and restart the Kaspersky Security Center Administration Console.
For more details on access rights to Kaspersky Security Center objects, please refer to the Kaspersky Security Center documentation.
Page top