Contents
The help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Control
This section contains information about how to remotely monitor mobile devices in the Administration Console of Kaspersky Security Center.
The help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Configuring restrictions
This section provides instructions on how to configure user access to the features of mobile devices.
The help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Special considerations for devices running Android version 10 and later
Android 10 introduced numerous changes and restrictions targeting API 29 or higher. Some of these changes affect the availability or functionality of some of the app's features. These considerations apply only to devices running Android 10 or later.
Ability to enable, disable, and configure Wi-Fi
- Wi-Fi networks can be added, deleted, and configured in the Administration Console of Kaspersky Security Center. When a Wi-Fi network is added to a policy, Kaspersky Endpoint Security receives this network configuration when it first connects to Kaspersky Security Center.
- When a device detects a network configured through Kaspersky Security Center, Kaspersky Endpoint Security prompts the user to connect to that network. If the user chooses to connect to the network, all of the settings configured through Kaspersky Security Center are automatically applied. The device then automatically connects to that network when in range, without showing further notifications to the user.
- If a user's device is already connected to another Wi-Fi network, sometimes the user may not be prompted to approve a network addition. In such cases, the user must turn Wi-Fi off and on again to receive the suggestion.
- When Kaspersky Endpoint Security suggests a user connect to a Wi-Fi network and the user refuses to do so, the app's permission to change the Wi-Fi state is revoked. Kaspersky Endpoint Security then cannot suggest connecting to Wi-Fi networks until the user grants the permission again by going to Settings → Apps & notifications → Special App access → Wi-Fi Control → Kaspersky Endpoint Security.
- Only open networks and networks encrypted with WPA2-PSK are supported. WEP and WPA encryption are not supported.
- If the password for a network previously suggested by the app is changed, the user must manually delete that network from the list of known networks. The device will then be able to receive a network suggestion from Kaspersky Endpoint Security and connect to it.
- When a device OS is updated from Android version 9 or earlier to Android version 10 or later, and/or Kaspersky Endpoint Security installed on a device running Android version 10 or later is updated, the networks that were previously added via Kaspersky Security Center cannot be modified or deleted through Kaspersky Security Center policies. The user, however, can manually modify or delete such networks in the device settings.
- On devices running Android 10, a user is prompted for the password during an attempt to connect manually to a protected suggested network. Automatic connection does not require entering the password. If a user's device is connected to some other Wi-Fi network, the user must first disconnect from that network to connect automatically to one of the suggested networks.
- On devices running Android 11, a user may manually connect to a protected network suggested by the app, without entering the password.
- When Kaspersky Endpoint Security is removed from a device, the networks previously suggested by the app are ignored.
- Prohibiting use of Wi-Fi networks is not supported.
Camera access
- On devices running Android 10, use of the camera cannot be completely prohibited. Prohibiting use of the camera for a work profile is still available.
- If a third-party app attempts to access the device's camera, that app will be blocked, and the user will be notified about the issue. However, the apps that use the camera while running in background mode cannot be blocked.
- When an external camera is disconnected from a device, a notification about the camera not being available may be displayed in some cases.
Managing screen unlock methods
- Kaspersky Endpoint Security now resolves the password strength requirements into one of the system values: medium or high.
- If the password length required is 1 to 4 symbols, then the app prompts the user to set a medium-strength password. It must be either numeric (PIN), with no repeating or ordered (e.g. 1234) sequences; or alphanumeric. The PIN or password must be at least 4 characters long.
- If the password length required is 5 or more symbols, then the app prompts the user to set a high-strength password. It must be either numeric (PIN), with no repeating or ordered sequences; or alphanumeric (password). The PIN must be at least 8 digits long; the password must be at least 6 characters long.
- Using a fingerprint to unlock the screen can be managed for a work profile only.
The help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Configuring restrictions for Android devices
To keep an Android device secure, configure the Wi-Fi, camera, and Bluetooth usage settings on the device.
By default, the user can use Wi-Fi, camera, and Bluetooth on the device without restrictions.
To configure the Wi-Fi, camera, and Bluetooth usage restrictions on the device:
- In the console tree, in the Managed devices folder, select the administration group to which the Android devices belong.
- In the workspace of the group, select the Policies tab.
- Open the policy properties window by double-clicking any column.
Complete the following steps within 15 minutes. Otherwise, you may face an error when saving changes to the policy.
- In the policy Properties window, select the Device Management section.
- In the Restrictions section, configure usage of Wi-Fi, camera, and Bluetooth:
- To disable the Wi-Fi module on the user's mobile device, select the Prohibit use of Wi-Fi check box.
On devices running Android 10.0 or later, prohibiting the use of Wi-Fi networks is not supported.
- To disable the camera on the user's mobile device, select the Prohibit use of camera check box.
When camera usage is prohibited, the app displays a notification upon opening and then closes shortly after. On Asus and OnePlus devices, the notification is shown in full screen. The device user can tap the Close button to exit the app.
On devices running Android 11 or later, Kaspersky Endpoint Security for Android must be set as an Accessibility feature. Kaspersky Endpoint Security for Android prompts the user to set the app as an Accessibility feature through the Initial Configuration Wizard. The user can skip this step or disable this service in the device settings at a later time. If this is the case, you will not be able to restrict use of the camera.
- To disable Bluetooth on the user's mobile device, select the Prohibit use of Bluetooth check box.
On Android 12 or later, the use of Bluetooth can be disabled only if the device user granted the Nearby Bluetooth devices permission. The user can grant this permission during the Initial Configuration Wizard or at a later time.
On personal devices running Android 13 or later, the use of Bluetooth cannot be disabled.
- To disable the Wi-Fi module on the user's mobile device, select the Prohibit use of Wi-Fi check box.
- Click the Apply button to save the changes you have made.
Mobile device settings are configured after the next device synchronization with the Kaspersky Security Center.
Page topThe help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Configuring iOS MDM device feature restrictions
To ensure compliance with corporate security requirements, configure restrictions on the operation of the iOS MDM device. For information about available restrictions, refer to the context help of the administration plug-in.
To configure iOS MDM device feature restrictions:
- In the console tree, in the Managed devices folder, select the administration group to which the iOS MDM devices belong.
- In the workspace of the group, select the Policies tab.
- Open the policy properties window by double-clicking any column.
Complete the following steps within 15 minutes. Otherwise, you may face an error when saving changes to the policy.
- In the policy Properties window, select the Features Restriction section.
- In the Features restriction settings section, select the Apply settings on device check box.
- Configure iOS MDM device feature restrictions.
- Click the Apply button to save the changes you have made.
- Select the Restrictions for applications section.
- In the Applications restriction settings section, select the Apply settings on device check box.
- Configure restrictions for apps on the iOS MDM device.
- Click the Apply button to save the changes you have made.
- Select the Restrictions for Media Content section.
- In the Media content restriction settings section, select the Apply settings on device check box.
- Configure restrictions for media content on the iOS MDM device.
- Click the Apply button to save the changes you have made.
As a result, once the policy is applied, restrictions on features, apps, and media content will be configured on the user's mobile device.
Page topThe help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Configuring user access to websites
This section contains instructions on how to configure access to websites on Android and iOS devices.
The help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Configuring access to websites on Android devices
You can use Web Protection to configure access of Android device users to websites. Web Protection supports website filtering by categories defined in Kaspersky Security Network cloud service. Filtering allows you to restrict user access to certain websites or categories of websites (for example, those from the "Gambling, lotteries, sweepstakes", or "Internet communication" categories). Web Protection also protects the personal data of users on the internet.
To enable Web Protection:
- Kaspersky Endpoint Security must be enabled as an Accessibility Features service.
- The Statement regarding data processing for the purpose of using Web Protection (Web Protection Statement) should be accepted. Kaspersky Endpoint Security uses Kaspersky Security Network (KSN) to scan websites. The Web Protection Statement contains the terms of data exchange with KSN.
You can accept the Web Protection Statement for the user in Kaspersky Security Center. In this case, the user is not required to take any action.
If you have not accepted the Web Protection Statement and prompt the user to do this, the user must read and accept the Web Protection Statement in the app settings.
If you have not accepted the Web Protection Statement, Web Protection is not available.
Web Protection on Android devices works only in the Google Chrome browser (including the Custom Tabs feature), Huawei Browser, and Samsung Internet Browser. Web Protection for Huawei Browser and Samsung Internet Browser does not block sites on a mobile device if a work profile is used and Web Protection is enabled only for the work profile.
Web Protection is enabled by default: user access to websites in the Phishing and Malware categories is blocked.
To configure the settings of the device user's access to websites:
- In the console tree, in the Managed devices folder, select the administration group to which the Android devices belong.
- In the workspace of the group, select the Policies tab.
- Open the policy properties window by double-clicking any column.
Complete the following steps within 15 minutes. Otherwise, you may face an error when saving changes to the policy.
- In the policy Properties window, select the Web Protection.
- To use Web Protection, you or device user must read and accept the Statement regarding data processing for the purpose of using Web Protection (Web Protection Statement):
- Click the Web Protection Statement link at the top of the section.
This opens Statement regarding data processing for purpose of using Web Protection window.
- Read and accept Privacy Policy by selecting the corresponding check box. To view Privacy Policy, click the Privacy Policy link.
If you do not accept Privacy Policy, mobile device user can accept Privacy Policy in the Initial Configuration Wizard or in the app (
 → About → Terms and conditions → Privacy Policy).
→ About → Terms and conditions → Privacy Policy). - Select the Web Protection Statement acceptance mode:
- I have read and accept the Web Protection Statement
- Request acceptance of the Web Protection Statement from the device user
- I do not accept the Web Protection Statement
If you select I do not accept the Web Protection Statement, the Web Protection does not block sites on a mobile device. Mobile device user cannot enable Web Protection in the Kaspersky Endpoint Security.
- Click OK to close the window.
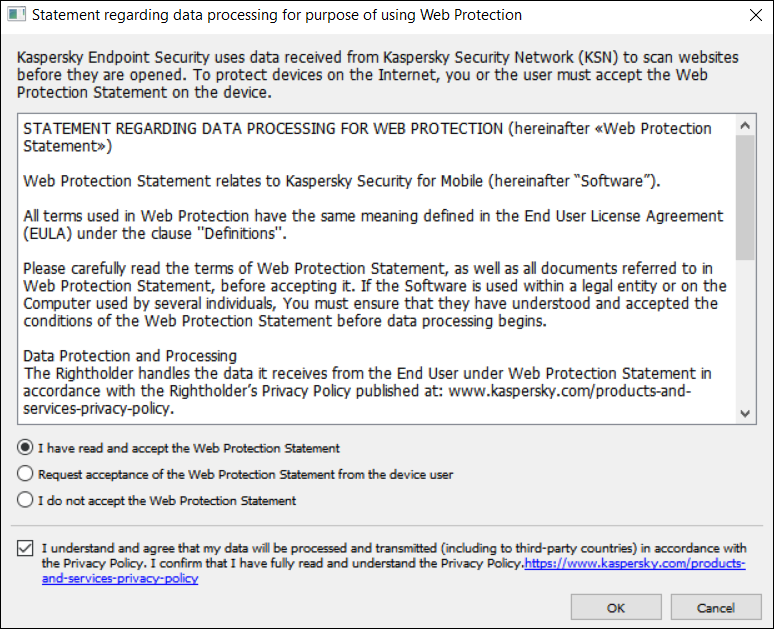
Step 5. Accept the Statement regarding data processing for purpose of using Web Protection.
- Click the Web Protection Statement link at the top of the section.
- Select the Enable Web Protection check box.
- If you want the app to check a full URL when opening a website in Custom Tabs, select the Check full URL when using Custom Tabs check box.
This option provides better detection of a URL and its check against the configured Web Protection rules.
- Select one of the following options:
- If you want the app to restrict user access to websites depending on their content, do the following:
- In the Web Protection section, in the drop-down list select Websites of selected categories are forbidden.
- Create a list of blocked categories by selecting check boxes next to the categories of websites to which the app will block access.

Step 8. Web Protection section. Select the categories of websites to block access to.
- If you want the app to allow or restrict user access only to websites specified by the administrator, do the following:
- In the Web Protection section, in the drop-down list select Only listed websites are allowed or Only listed websites are blocked.
- Create a list of websites by adding addresses of websites to which the app will allow or block access, depending on the value selected in the drop-down list. You can add websites by link (full URL, including the protocol, e.g.
https://example.com).To make sure that the app allows or blocks access to the specified website in all supported versions of Google Chrome, include the same URL twice, once with the HTTP protocol (e.g., http://example.com) and once with the HTTPS protocol (e.g., https://example.com).
The app also supports regular expressions. When entering the address of an allowed or blocked website, use the following templates:
https://example\.com/.*—All child pages of the website are allowed (for example,https://example.com/about).https://.*\.example\.com—All subdomain pages of the website are allowed (for example,https://pictures.example.com).
Use the expression
https?to select the HTTP and HTTPS protocols. For more details on regular expressions, please refer to the Oracle Technical Support website.
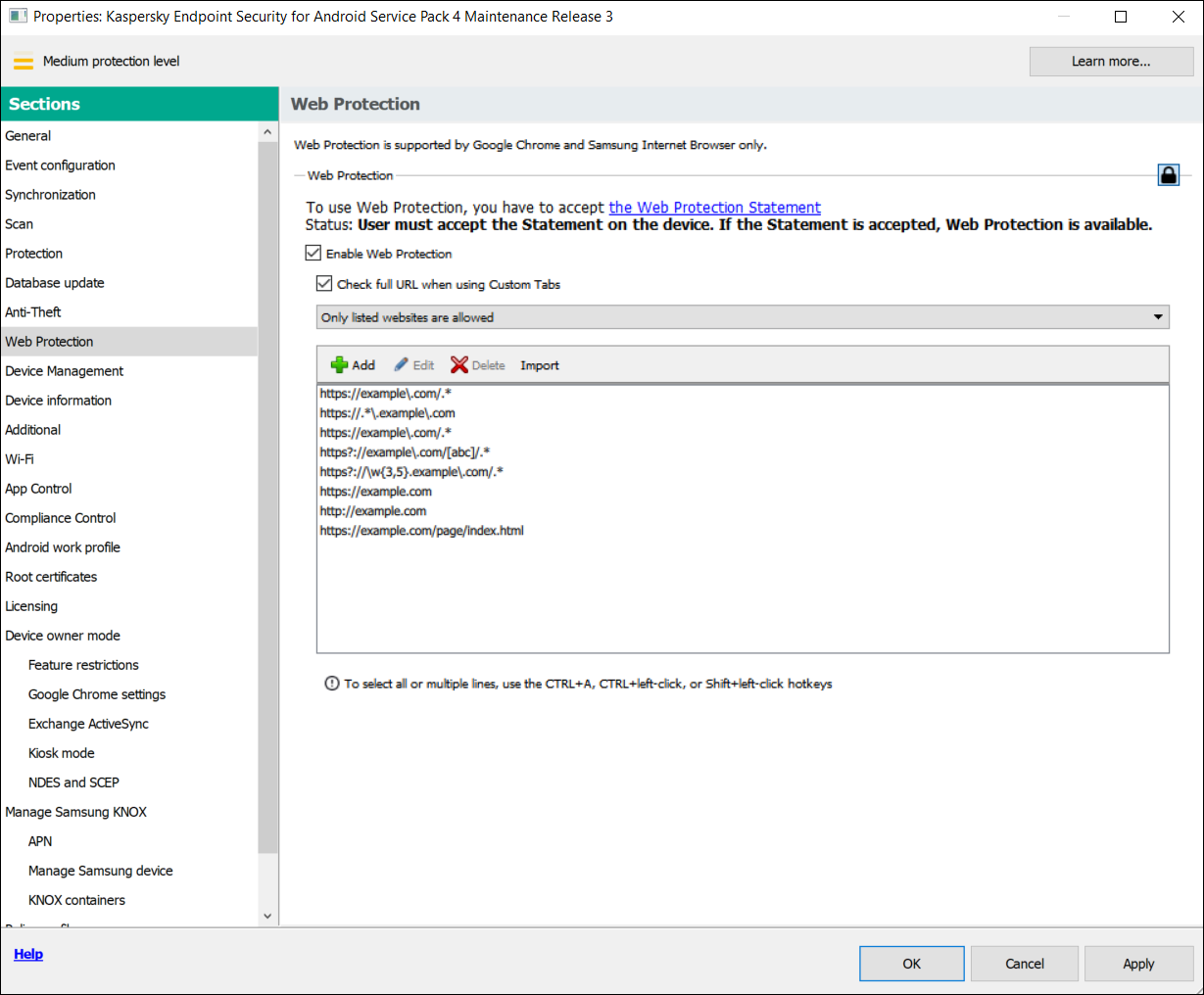
Step 9. Web Protection section. Specify the list of websites to allow access to.
- If you want the app to block user access to all websites, in the Web Protection section, in the drop-down list, select All websites are blocked.
- If you want the app to restrict user access to websites depending on their content, do the following:
- To lift content-based restrictions on user access to websites, clear the Enable Web Protection check box.
- Click the Apply button to save the changes you have made.
Mobile device settings are configured after the next device synchronization with the Kaspersky Security Center.
Managing the website list
You can manage the list of websites with the following buttons:
- Add - Click to add a website to the list by entering a URL or regular expression.
- Import - Click to add multiple websites to the list by specifying a
.txtfile which contains the required URLs or regular expressions. The file must be encoded in UTF-8. URLs or regular expressions in the file must be separated by semicolons or by line breaks. - Edit - Click to change the address of a website.
- Delete - Click to remove a website from the list. To remove multiple websites from the list, select them with the CTRL+A, CTRL+left-click, or SHIFT+left-click hotkeys, and then click Delete.
The help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Configuring access to websites on iOS MDM devices
Configure Web Protection settings to control access to websites for iOS MDM device users. Web Protection controls a user's access to websites based on lists of allowed and blocked websites. Web Protection also lets you add website bookmarks on the bookmark panel in Safari.
By default, access to websites is not restricted.
Web Protection settings can be configured for supervised devices only.
To configure access to websites on the user's iOS MDM device:
- In the console tree, in the Managed devices folder, select the administration group to which the iOS MDM devices belong.
- In the workspace of the group, select the Policies tab.
- Open the policy properties window by double-clicking any column.
Complete the following steps within 15 minutes. Otherwise, you may face an error when saving changes to the policy.
- In the policy Properties window, select the Web Protection section.
- In the Web Protection settings section, select the Apply settings on device check box.
- To block access to blocked websites and allow access to allowed websites:
- In the Web Filter Mode drop-down list, select the Limit adult content mode.
- In the Allowed websites section, create a list of allowed websites.
The website address should begin with
"http://"or"https://". Kaspersky Device Management for iOS allows access to all websites in the domain. For example, if you have added http://www.example.com to the list of allowed websites, access is allowed to http://pictures.example.com and http://example.com/movies. If the list of allowed websites is empty, the application allows access to all websites other than those included in the list of blocked websites. - In the Forbidden websites section, create a list of blocked websites.
The website address should begin with
"http://"or"https://". Kaspersky Device Management for iOS blocks access to all websites in the domain.
- To block access to all websites other than allowed websites on the tab list:
- In the Web Filter Mode drop-down list, select the Allow bookmarked websites only mode.
- In the Bookmarks section, create a list of bookmarks of allowed websites.
The website address should begin with
"http://"or"https://". Kaspersky Device Management for iOS allows access to all websites in the domain. If the bookmark list is empty, the application allows access to all websites. Kaspersky Device Management for iOS adds websites from the list of bookmarks on the bookmarks tab in Safari in the user's mobile device.
- Click the Apply button to save the changes you have made.
As a result, once the policy is applied, Web Protection will be configured on the user's mobile device according to the mode selected and lists created.
Page topThe help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Compliance control
This section contains instructions on how to monitor device compliance with corporate requirements and how to configure compliance control rules.
The help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Compliance control of Android devices with corporate security requirements
You can control Android devices for compliance with the corporate security requirements. Corporate security requirements regulate how the user can work with the device. For example, the real-time protection must be enabled on the device, the anti-virus databases must be up-to-date, and the device password must be sufficiently strong. Compliance control is based on a list of rules. A compliance rule includes the following components:
- Device check criterion (for example, absence of blocked apps on the device).
- Time period allocated for the user to fix the non-compliance (for example, 24 hours).
- Actions that will be taken on the device if the user does not fix the non-compliance within the set time period (for example, lock the device).
On Android 12 or later, the app may perform this task later than specified if the device is in battery saver mode.
To create a rule for checking devices for compliance with a group policy:
- In the console tree, in the Managed devices folder, select the administration group to which the Android devices belong.
- In the workspace of the group, select the Policies tab.
- Open the policy properties window by double-clicking any column.
Complete the following steps within 15 minutes. Otherwise, you may face an error when saving changes to the policy.
- In the policy Properties window, select the Compliance Control section.
- To receive notifications about devices that do not comply with the policy, in the Non-compliance notification section select the Notify administrator check box.
If the device does not comply with a policy, during device synchronization with the Administration Server, Kaspersky Endpoint Security for Android writes an entry for Violation detected: <name of the criterion checked> in the event log. You can view the Event log on the Events tab in the Administration Server properties or in the local properties of the application.
- To notify the device user that the user's device does not comply with the policy, in the Non-compliance notification section select the Notify user check box.
If the device does not comply with a policy, during device synchronization with the Administration Server, Kaspersky Endpoint Security for Android notifies the user about this.
- In the Compliance Control rules section, compile a list of rules for checking the device for compliance with the policy.
- To add a rule, click Add.
The Compliance Rule Wizard starts. Proceed through the wizard by using the Next button.
- Select a non-compliance criterion for the rule.
The following criteria are available:
- Real-time protection is disabled
Checks whether the security app is not installed on the device or is not running.
- Anti-Virus databases are out of date
Checks whether the Anti-Virus databases were last updated 3 or more days ago.
- Forbidden apps are installed
Checks whether the list of apps on the device contains apps that are set as forbidden in the App Control.
- Apps from forbidden categories are installed
Checks whether the list of apps on the device contains apps from the categories that are set as forbidden in the App Control.
- Not all required apps are installed
Checks whether the list of apps on the device does not contains an app that is set as required in the App Control.
- Operating system version is out of date
Checks whether the Android version on the device is within the allowed range.
For this criterion, specify the minimum and maximum allowed versions of Android. If the maximum allowed version is set to Any, it means that future Android versions supported by Kaspersky Endpoint Security for Android will also be allowed.
- Device has not been synchronized for a long time
Checks how long ago the device last synchronized with Administration Server.
For this criterion, specify the maximum period after the last sync.
- Device has been rooted
Checks whether the device is hacked (whether root access is gained on the device).
- Unlock password is not compliant with security requirements
Checks whether the unlock password on the device does not comply with the settings defined in the Device Management section of the policy.
- Installed version of Kaspersky Endpoint Security for Android is not supported
Checks whether the security application installed on the device is not obsolete.
For this criterion, specify the minimum allowed version of Kaspersky Endpoint Security for Android.
- SIM card usage is not compliant with security requirements
Checks whether the device SIM card has been replaced or removed compared to the previous check state.
You can also enable the check for inserting an additional SIM card.
In some cases, replacement, removal, and insertion of an eSIM is also checked.
- Real-time protection is disabled
- Select the actions to be performed on the device if the specified non-compliance criterion is detected. You can add multiple actions. They are combined by the AND logical operator.
The following actions are available:
- Block all apps except system ones
All apps on the user's mobile device, except system apps, are blocked from starting.
As soon as the non-compliance criterion selected for the rule is no longer detected on the device, the apps are automatically unblocked.
- Lock device
Mobile device is locked. To obtain access to data, you must unlock the device. If the reason for locking the device is not rectified after the device is unlocked, the device will be locked again after the specified time period.
- Wipe corporate data
Android work profile, the corporate email account, settings for connecting to the corporate Wi-Fi network and VPN, Access Point Name (APN), KNOX container, and the KNOX License Manager key are wiped.
- Full reset
All data is deleted from the mobile device and the settings are rolled back to their factory values. After this action is completed, the device will no longer be a managed device. To connect the device to Kaspersky Security Center, you must reinstall Kaspersky Endpoint Security for Android.
- Lock work profile
The work profile on the device is locked. To obtain access to the work profile, you must unlock it. If the reason for locking the work profile is not rectified after it is unlocked, the work profile will be locked again after the specified time period.
The action is only applicable to Android 6+.
After the work profile on a device is locked, the history of work profile passwords is cleared. It means that the user can specify one of the recent passwords, regardless of the work profile password settings.
The new rule appears in the Compliance Control rules section.
- Block all apps except system ones
- To temporarily disable a rule that you have created, use the toggle switch opposite the selected rule.
- Click the Apply button to save the changes you have made.
Mobile device settings are configured after the next device synchronization with the Kaspersky Security Center. If the user device does not comply with the rules, the restrictions you have specified in the scan rule list are applied to the device.
Page topThe help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Compliance control of iOS MDM devices with corporate security requirements
Compliance Control allows you to monitor iOS MDM devices for compliance with corporate security requirements and take actions if non-compliance is found. Compliance Control is based on a list of rules. Each rule includes the following components:
- Status (whether the rule is enabled or disabled).
- Non-compliance criteria (for example, absence of the specified apps or operating system version).
- Actions performed on the device if non-compliance is found (for example, wipe corporate data or send an email message to the user).
To create a rule:
- In the console tree, in the Managed devices folder, select the administration group to which the iOS MDM devices belong.
- In the workspace of the group, select the Policies tab.
- Open the policy properties window by double-clicking any column.
Complete the following steps within 15 minutes. Otherwise, you may face an error when saving changes to the policy.
- In the policy Properties window, select the Compliance Control section.
- In the Compliance Control rules section, click Add.
The Compliance Control Rule Wizard starts.
- Select the Enable rule check box if you want to activate the rule. If the check box is cleared, the rule is disabled.
- On the Non-compliance criteria tab, click Add criterion and select a non-compliance criterion for the rule. You can add multiple criteria. They are combined by the AND logical operator.
The following criteria are available:
- List of apps on device
Checks whether the list of apps on the device contains forbidden apps or does not contain required apps.
For this criterion, you need to select a check type (Contains or Does not contain) and specify the app's bundle ID. How to get the bundle ID of an app
- Operating system version
Checks the version of the operating system on the device.
For this criterion, you need to select a comparison operator (Equal to, Not equal to, Less than, Less than or equal to, Greater than, or Greater than or equal to) and specify the iOS version.
Note that the Equal to and Not equal to operators check for a full match of the operating system version with the specified value. For instance, if you specify 15 in the rule, but the device is running iOS 15.2, the Equal to criterion is not met. If you need to specify a range of versions, you can create two criteria and use the Less than and Greater than operators.
- Management mode
Checks the device's management mode.
For this criterion, you need to select a mode (Supervised device or Non-supervised device).
- Device type
Checks the device type.
For this criterion, you need to select a type (iPhone or iPad).
- Device model
Checks the device model.
For this criterion, you need to select an operator (Included in the list or Not included in the list), and then specify models that will be checked or excluded from the check, respectively.
To specify a model, type at least one character in the Identifier field, and then select the required model from the appeared list. The list contains mobile device codes and their matching product names. For example, if you want to add all iPhone 14 models, type "iPhone 14". In this case, you can select any of the available models: "iPhone 14", "iPhone 14 Plus", "iPhone 14 Pro", "iPhone 14 Pro Max".
In some cases, the same product name may correspond to several mobile device codes (for example, the "iPhone 7" product name corresponds to two mobile device codes, "iPhone9,1" and "iPhone9,3"). Be sure that you select all of the mobile device codes that correspond to the required models.
If you type a value that is not on the list, nothing will be found. However, you can click the OK button in the field to add the typed value to the criterion.
- Device is roaming
Checks whether the device is roaming (if you select True) or not (if you select False).
- Device password is set
Checks whether a password is set (if you select True) or not (if you select False).
If you select True, select whether the device password must match (if you select Matches policy) or must not match (if you select Does not match policy) the settings specified in the Password Settings section.
- Device free space
Checks whether the amount of free space on the device becomes less than the threshold that you specify.
For this criterion, specify the threshold amount of free space, and then select the measurement unit (GB or MB).
- Device is not encrypted
Checks whether the device is not encrypted.
Data encryption is enabled by default on password-locked iOS devices (Settings → Touch ID / Face ID and Password → Enable Password). Also, the hardware encryption on a device must be set to At block and file level (you can check this parameter in the device properties: in the console tree, select Additional → Mobile Device Management → Mobile devices, and then double-click the required device).
- SIM card is changed
Checks whether the device SIM card has been replaced, inserted, or removed compared to the previous check state.
- Last sync earlier than
Checks how long ago the device last synchronized with Administration Server.
For this criterion, specify the maximum time after the last sync, and then select the measurement unit (Hours or Days).
We do not recommend that you specify a value less than the value of the Updating frequency for information about devices parameter in the iOS MDM Server settings.
If you specify criteria that contradict each other (for example, Device type is set to iPhone but the list of values of Device model, with the Included in the list operator selected, contains an iPad model), an error message is displayed. You cannot save such a rule.
- List of apps on device
- On the Actions tab, specify actions to be performed on the device if all specified non-compliance criteria are detected.
Actions are performed during the compliance rule check, which happens every 40 minutes, and persist until the next synchronization with the Administration Server. To prevent repetitive actions from a single non-compliance detection, set the Updating frequency for information about devices parameter in the iOS MDM Server settings to 30 minutes.
Add an action in one of the following ways:
- Click the Add action button if the action should be taken on the device immediately after non-compliance is detected.
- Click the Add postponed action button if you want to also set a time period in which the user can fix the non-compliance. If the non-compliance is not fixed within this period, the action is performed on the device.
The following actions are available:
- Send email message to user
The device user is informed about the non-compliance by email.
For this action, you need to specify the user's email address(es). If necessary, you can edit the default text of the email message.
- Wipe corporate data
All installed configuration profiles, provisioning profiles, the iOS MDM profile, and applications for which the Remove together with iOS MDM profile check box has been selected are removed from the device. This action is performed by sending the Wipe corporate data command.
- Install profile
The configuration profile is installed on the device. This action is performed by sending the Install profile command.
For this action, you need to specify the ID of the configuration profile to be installed.
When the non-compliance criteria selected for the rule are no longer detected on the device, you can revert the action by sending the respective command to the device.
- Delete profile
The configuration profile is deleted from the device. This action is performed by sending the Remove profile command.
For this action, you need to specify the ID of the configuration profile to be removed.
When the non-compliance criteria selected for the rule are no longer detected on the device, you can revert the action by sending the respective command to the device.
- Delete all profiles
All previously installed configuration profiles are deleted from the device.
When the non-compliance criteria selected for the rule are no longer detected on the device, you can install the deleted configuration profiles one by one, by sending the respective command to the device.
- Update operating system
The device operating system is updated.
For this action, you need to select the specific operation (Download and install, Download only, or Install only if you want to install a previously downloaded version) and the iOS version to be downloaded and/or installed.
- Change Bluetooth settings (supervised only)
For this action, you need to select whether you want to enable or disable Bluetooth on the device.
When the non-compliance criteria selected for the rule are no longer detected on the device, you can revert the action by sending the respective command to the device.
- Reset to factory settings
All data is deleted from the device and the settings are rolled back to their default values.
- Delete managed app
For this action, you need to specify the bundle ID of the managed app that you want to delete from the device. An app is considered managed if it has been installed on a device through Kaspersky Security Center. How to get the bundle ID of an app
When the non-compliance criteria selected for the rule are no longer detected on the device, you can revert the action by sending the respective command to the device.
- Delete all managed apps
All managed apps are deleted from the device. An app is considered managed if it has been installed on a device through Kaspersky Security Center.
When the non-compliance criteria selected for the rule are no longer detected on the device, you can install the deleted apps one by one, by sending the respective command to the device.
- Delete profile(s) of specified type
For this action, you need to select the type of the profile to be deleted from the device (for example, Web Clips or Calendar subscriptions).
As soon as the non-compliance criteria selected for the rule are no longer detected on the device, the deleted profiles are automatically restored.
- Change roaming settings
For this action, you need to select whether you want to enable or disable data roaming on the device.
When the non-compliance criteria selected for the rule are no longer detected on the device, you can revert the action by sending the respective command to the device.
If you specify actions that contradict each other (for example, Enable Bluetooth and Disable Bluetooth at the same time, an error message is displayed. You cannot save such a rule.
- Click the OK button to save the rule and close the wizard.
The new rule appears in the list in the Compliance Control rules section.
- Click the Apply button to save the changes you have made to the policy and exit the policy properties window.
Mobile device settings are configured after the next device synchronization with the Kaspersky Security Center.
Page topThe help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
App control
This section contains instructions on how to configure user access to apps on a mobile device.
The help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
App control on Android devices
The App Control component allows you to manage apps on Android devices to keep these devices secure.
- You can impose restrictions on the user's activity on a device on which blocked apps are installed or required apps are not installed (for example, lock the device). You can impose restrictions using the Compliance Control component. To do so, in the scan rule settings, you must select the Forbidden apps are installed, Apps from forbidden categories are installed, or Not all required apps are installed criterion.
Kaspersky Endpoint Security for Android must be set as an Accessibility feature to ensure proper functioning of App Control. Kaspersky Endpoint Security for Android prompts the user to set the app as an Accessibility feature through the Initial Configuration Wizard. The user can skip this step or disable this service in the device settings at a later time. If this is the case, App Control does not run.
In device owner mode, you have extended control over the device. App Control operates without notifying the device user:
- Required apps are installed automatically in the background. To install apps silently, you need to specify a link to the APK file of the required app in the policy settings.
- Forbidden apps can be deleted from the device automatically. To delete apps silently, you need to select the Delete blocked apps automatically (in device owner mode only) check box in the policy settings.
To configure the settings of app startup on the mobile device:
- In the console tree, in the Managed devices folder, select the administration group to which the Android devices belong.
- In the workspace of the group, select the Policies tab.
- Open the policy properties window by double-clicking any column.
Complete the following steps within 15 minutes. Otherwise, you may face an error when saving changes to the policy.
- In the policy Properties window, select the App Control section.
- In the Operation mode section, select the mode of app startup on the user's mobile device:
- To allow the user to start all apps except those specified in the list of categories and apps as blocked apps, select the Blocked apps mode. The app will hide blocked app icons.
- To allow the user to start only apps specified in the list of categories and apps as allowed, recommended, or required apps, select the Allowed apps mode. The app will hide all app icons except those specified in the list of allowed, recommended, or required apps and system apps.
- If you want Kaspersky Endpoint Security for Android to send data on forbidden apps to the event log without blocking them, select the Do not block forbidden apps, write to event log only check box.
During the next synchronization of the user's mobile device with the Administration Server, Kaspersky Endpoint Security for Android writes an entry for A forbidden app has been installed in the event log. You can view the Event log on the Events tab in the Administration Server properties or in the local properties of the application.
- If the device is in device owner mode, select the Delete blocked apps automatically (in device owner mode only) check box to remove forbidden apps from the device in the background without notifying the user.
- If you want Kaspersky Endpoint Security for Android to block the startup of system apps on the user's mobile device (such as Calendar, Camera, and Settings) in Allowed apps mode, select the Block system apps check box.
Kaspersky experts recommend against blocking system apps because this could lead to failures in device operation (the device may stop responding to user actions or start continuous reboot). To restore normal operation of the device, the user should reset it to factory settings in recovery mode (the procedure is vendor-specific).
- Create a list of categories and apps to configure startup of apps.
Mobile app packages previously created in the Kaspersky Security Center can be added to the list. How to get the package name of an app
For details on app categories, please refer to the Appendices.
For a list of the apps that belong to each category, please visit the Kaspersky website.
- Click the Apply button to save the changes you have made.
Mobile device settings are configured after the next device synchronization with the Kaspersky Security Center.
Page topThe help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
App control on iOS MDM devices
Kaspersky Security Center allows you to manage apps on iOS MDM devices to keep these devices secure. You can create a list of apps allowed to be installed on devices and a list of apps prohibited from being displayed and launching on devices.
These restrictions apply only to supervised iOS MDM devices.
Open Restrictions for applications section
To open settings for app restrictions on iOS MDM devices:
- In the console tree, in the Managed devices folder, select the administration group to which the iOS MDM devices belong.
- In the workspace of the group, select the Policies tab.
- Open the policy properties window by double-clicking any column.
Complete the following steps within 15 minutes. Otherwise, you may face an error when saving changes to the policy.
- In the policy Properties window, select the Restrictions for applications section.
Restrict app installation
By default, the user can install any apps on the supervised iOS MDM device.
To restrict the apps that can be installed on the device:
- Select the Allow installation of apps from the list (supervised only) check box.
- In the table, click Add to add an app to the list.
- Specify the app's bundle ID. Specify the
com.apple.webappvalue to allow all web clips. How to get the bundle ID of an app - Click the Apply button to save the changes you have made.
Once the policy is applied to a device, the specified restrictions for apps are configured on the device. Only apps from the list and system apps will be available for installation. All other apps can't be installed on the device.
The specified apps can be installed on the device in the following ways (if the corresponding options are enabled in the Features restrictions section):
- Installation from Apple Configurator or iTunes
- Installation from App Store
- Automatic loading
Specify prohibited apps
By default, all apps can be displayed and launched on the supervised iOS MDM device.
To specify prohibited apps:
- Select the Prohibit displaying and launching apps from the list (supervised only) check box.
- In the table, click Add to add an app to the list.
- Specify the app's bundle ID. Specify the
com.apple.webappvalue to restrict all web clips. How to get the bundle ID of an app - Click the Apply button to save the changes you have made.
Once the policy is applied to a device, the specified restrictions for apps are configured on the device. Apps from the list will be prohibited from being displayed and launching on the device. All other apps will be displayed and available to run.
Page topThe help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Installation and uninstallation of apps on a group of iOS MDM devices
Kaspersky Security Center allows you to install and remove apps on iOS MDM devices by sending commands to these devices.
Selecting devices
To select iOS MDM devices on which apps should be installed or removed:
- In the Mobile Device Management folder in the console tree, select the Mobile devices subfolder.
The folder workspace displays a list of managed mobile devices.
- In the workspace, filter iOS MDM devices by protocol type (iOS MDM).
- Select the iOS MDM device on which apps should be installed or removed.
You can also select multiple devices and send commands simultaneously. To select a group of devices, do one of the following:
- To select all devices in the workspace, filter the list of devices as required and press Ctrl+A.
- To select a range of devices, hold down the Shift key, click the first device in the range, and then click the last device in the range.
- To select individual devices, hold down the Ctrl key and click devices you want to include in the group.
Installing apps on devices
Before installing an app on an iOS MDM device, you must add that app to an iOS MDM Server. For more information, refer to Adding a managed app.
To install apps on selected iOS MDM devices:
- Right-click the selected devices. In the context menu that appears, select All commands, and then select Install app.
For a single device, you can also select Show command log in the context menu, proceed to the Install app section, and click the Send command button.
The Select apps window opens showing a list of managed apps.
- Select the apps you want to install on iOS MDM devices. To select a range of apps, use the Shift key. To select multiple apps individually, use the Ctrl key.
- Click OK to send the command to the devices.
When the command is executed on a device, the selected apps are installed. If the command is successfully executed, the command log will show its current status as Completed.
Removing apps from devices
To remove apps from selected iOS MDM devices:
- Right-click the selected devices. In the context menu that appears, select All commands, and then select Remove app.
For a single device, you can also select Show command log in the context menu, proceed to the Remove app section, and click the Send command button.
The Remove apps window opens showing a list of previously installed apps.
- Select the apps you want to remove from iOS MDM devices. To select a range of apps, use the Shift key. To select multiple apps individually, use the Ctrl key.
- Click OK to send the command to the devices.
When the command is executed on a device, the selected apps are uninstalled. If the command is successfully executed, the command log will show its current status as Completed.
The help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Software inventory on Android devices
You can inventory apps on Android devices connected to Kaspersky Security Center. Kaspersky Endpoint Security for Android receives information about all apps installed on mobile devices. Information acquired during inventory is displayed in the device properties in the Events section. You can view detailed information on each installed app, including its version and publisher.
To enable software inventory:
- In the console tree, in the Managed devices folder, select the administration group to which the Android devices belong.
- In the workspace of the group, select the Policies tab.
- Open the policy properties window by double-clicking any column.
Complete the following steps within 15 minutes. Otherwise, you may face an error when saving changes to the policy.
- In the policy Properties window, select the App Control section.
- In the Software inventory section, select the Send data on installed apps check box.
- Click the Apply button to save the changes you have made.
Mobile device settings are configured after the next device synchronization with the Kaspersky Security Center. Kaspersky Endpoint Security for Android sends data to the event log each time an app is installed or removed from the device.
Page topThe help for this version of the solution is no longer updated, so it may contain outdated information. For up-to-date information about the solution refer to the Kaspersky Secure Mobility Management 4.1 Help.
Configuring the display of Android devices in Kaspersky Security Center
For convenient operations with the list of mobile devices, you should configure the settings for displaying devices in Kaspersky Security Center. By default, the list of mobile devices is displayed in the Additional → Mobile Device Management → Mobile devices console tree. Device information is updated automatically. You can also manually update the list of mobile devices by clicking the Update button in the upper right corner.
After connecting the device to Kaspersky Security Center, devices are added to the mobile device list automatically. The mobile device list may contain detailed information about that device: model, operation system, IP address, and others.
You can configure the device name format and select the device status. The device status informs you about how the components of Kaspersky Endpoint Security for Android are operating on the user's mobile device.
Kaspersky Endpoint Security for Android components could be non-operational for the following reasons:
- The user disabled the component in the device settings.
- The user did not grant the app the necessary permissions for the component to operate (for example, there is no permission to determine the device location for the corresponding Anti-Theft command).
To display the device status, you must enable the Determined by the application condition in the administration group properties (Properties → Device status → Set device status to Critical if and Set device status to Warning if). In the administration group properties, you can also select other criteria for forming the mobile device status.
To configure the display of Android devices in Kaspersky Security Center:
- In the console tree, in the Managed devices folder, select the administration group to which the Android devices belong.
- In the workspace of the group, select the Policies tab.
- Open the policy properties window by double-clicking any column.
Complete the following steps within 15 minutes. Otherwise, you may face an error when saving changes to the policy.
- In the policy Properties window, select the Device information section.
- In the Device name in Kaspersky Security Center section, select the device name format for the device name in the Administration Console:
- Device model [email, device ID]
- Device model [email (if any) or device ID]
A device ID is a unique ID that Kaspersky Endpoint Security for Android generates from the data received from a device as follows:
- On personal devices running Android 9 and earlier, the app uses the IMEI. For later versions of Android, the app uses SSAID (Android ID) or checksum of other data received from the device.
- In device owner mode, the app uses IMEI on all Android versions.
- When a work profile is created on devices running Android 11 or earlier, the app uses IMEI. On other Android versions, the app uses the SSAID (Android ID) or checksum of other data received from the device.
- Set the Lock attribute in the locked position (
 ).
). - In the Device status in Kaspersky Security Center section, select the appropriate device status if a component of Kaspersky Endpoint Security for Android is not working:
 (Critical),
(Critical),  (Warning) or
(Warning) or  (OK).
(OK).In the list of mobile devices, the device status will be changed according to the selected status.
- Set the Lock attribute in the locked position.
- Click the Apply button to save the changes you have made.
Mobile device settings are configured after the next device synchronization with the Kaspersky Security Center.
Page top