Contents
About Kaspersky SD-WAN
Kaspersky SD-WAN is used to build Software-Defined Wide Area Networks (Software Defined WAN; SD-WAN). In SD-WAN networks, routes with the lowest latency and the greatest bandwidth are determined automatically. Traffic is routed using the SDN (Software Defined Networking) technology.
The SDN technology separates the
from the and allows managing the network infrastructure using an (using the web interface or the API). Separating the control plane from the data plane makes it possible to virtualize network functions (Network Function Virtualization; NFV), wherein network functions such as firewalls, routers, and load balancers are deployed on standard equipment. Network function virtualization in the solution is compliant with the NFV MANO specification (NFV Management and Network Orchestration) standards of the European Telecommunications Standards Institute (ETSI).Building an SD-WAN network does not depend on transport technologies. You can also send traffic over multiple links based on application requirements regarding bandwidth and quality of service. The following underlay network types are supported:
- MPLS transport networks
- Broadband links for connecting to the Internet
- Leased communication lines
- Wireless connections including 3G, 4G, and LTE
- Satellite links
The solution is intended for service providers and organizations with a large branch network; it replaces standard routers in distributed networks
(hereinafter referred to as CPE devices, CPEs).Kaspersky SD-WAN lets you do the following:
- Intelligent traffic management
- Automatic CPE device configuration
- Central management of solution components using the web interface
- Network monitoring
- Automatically responding to changes in QoS policies to meet requirements of applications
The figure below shows a diagram of an SD-WAN network built using the Kaspersky SD-WAN solution.
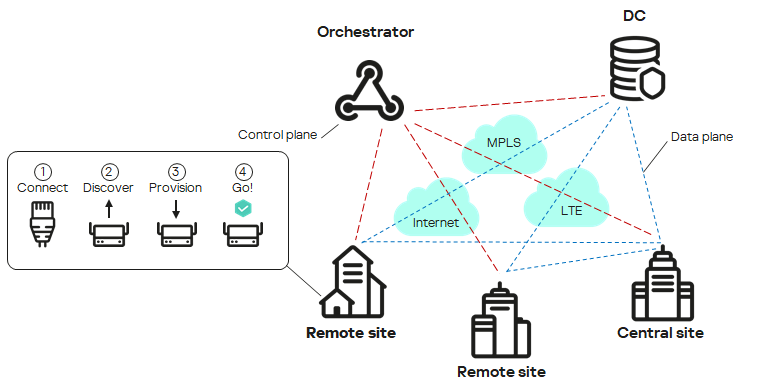 testtest
testtest
SD-WAN network diagram
Distribution kit
To learn more about purchasing the solution, please visit the Kaspersky website (https://www.kaspersky.com) or contact partner companies.
The distribution kit includes the following components:
- knaas-installer_<version information> in the TAR.GZ format (hereinafter also referred to as the installation archive) for solution deployment.
- Docker containers for deploying Kaspersky SD-WAN components:
- knaas-ctl
- knaas-orc
- knaas-www
- knass-vnfm
- knaas-vnfm-proxy
- mockpnf
You must download the following containers from the common Docker repository:
- mariaDB
- mongo
- redis
- syslog-ng
- zabbix-proxy-mysql
- zabbix-server-mysql
- zabbix-web-nginx-mysql
- CPE device firmware.
- A file with the text of the End User License Agreement, which stipulates the terms and conditions that you must accept to use the solution.
- Kaspersky SD-WAN Online Help files that let you read documentation without an Internet connection.
The content of the distribution kit may differ depending on the region in which the solution is distributed.
Page topHardware and software requirements
Kaspersky SD-WAN has the following hardware and software requirements:
Hardware requirements depend on the number of CPE devices being managed (see the recommended deployment scenarios below). If you need to calculate hardware requirements for a specific deployment scheme more precisely, we recommend contacting Kaspersky Technical Support.
1. Recommended computing resources for solution components version 2.4 and higher.
The following are supported specifications for instances of Kaspersky SD-WAN Orchestrator (ORC), Kaspersky SD-WAN Controller (CTL), the monitoring component (MON), and the Kaspersky Deployment Toolkit (KDT) utility; these are valid as long as identical components and software versions are used.
1.1. SD-WAN Orchestrator
Table 1. ORC instance type definitions
Instance type |
Number of CPE devices |
Specifications (approximate) |
||||
CPU* |
RAM |
Storage size** |
Storage IOPS** |
Network adapter |
||
Small ORC |
1000 |
16 cores |
32 GB |
256 GB |
3,000 |
2 x 1 Gbps |
Medium ORC |
5,000 |
24 cores |
64 GB |
512 GB |
5,000 |
2 x 1 Gbps |
Large ORC |
10,000 |
16 cores |
128 GB |
1 TB |
10,000 |
2 x 10 Gbps |
* CPU without Hyper-Threading. Recommendations:
- Xeon Silver 4314 for Small ORC instances
- Xeon Gold 5318Y, Xeon Gold 5418Y, or higher for Medium ORC instances
- Xeon Gold 6414U, Xeon Gold 6438Y+, or higher for Large ORC instances
** SSD
1.2. SD-WAN Controller
Table 2. CTL instance type definitions
Instance type |
Number of CPE devices |
Specifications (approximate) |
||||
CPU* |
RAM |
Storage size** |
Storage IOPS** |
Network adapter |
||
Small CTL |
250 |
16 cores |
32 GB |
64 GB |
3,000 |
2 x 1 Gbps |
Medium CTL |
500 |
24 cores |
48 GB |
128 GB |
5,000 |
2 x 1 Gbps |
Large CTL |
1000 |
32 cores |
64 GB |
256 GB |
10,000 |
2 x 10 Gbps |
* CPU without Hyper-Threading. Recommendations:
- Xeon Silver 4314 for Small CTL instances
- Xeon Gold 5318Y, Xeon Gold 5418Y, or higher for Medium CTL instances
- Xeon Gold 6414U, Xeon Gold 6438Y+, or higher for Large CTL instances
** SSD
1.3. SD-WAN monitoring component
Table 3. MON instance type definitions
Instance type |
Number of CPE devices |
Specifications (approximate) |
||||
CPU* |
RAM |
Storage size** |
Storage IOPS** |
Network adapter |
||
Small MON |
1,000 |
8 cores |
16 GB |
1 TB |
3,000 |
2 x 1 Gbps |
Medium MON |
5,000 |
24 cores |
64 GB |
5 TB |
5,000 |
2 x 1 Gbps |
Large MON |
10,000 |
16 cores |
96 GB |
10 TB |
10,000 |
2 x 10 Gbps |
* CPU without Hyper-Threading. Recommendations:
- Xeon Silver 4309Y for Small MON instances
- Xeon Gold 5318Y, Xeon Gold 5418Y, or higher for Medium MON instances
- Xeon Gold 6414U, Xeon Gold 6438Y+, or higher for Large MON instances
**SSD, RAID 10
1.4. SD-WAN All-in-One
An SD-WAN All-in-One (AIO) instance includes the following administration components: Kaspersky SD-WAN Orchestrator (ORC), Kaspersky SD-WAN Controller (CTL), and Kaspersky SD-WAN monitoring component (MON). The following instance specifications are supported:
Table 4. AIO instance type definitions
Instance type |
Number of CPE devices |
Specifications (approximate) |
||||
CPU* |
RAM |
Storage size** |
Storage IOPS** |
Network adapter |
||
Small AIO |
50 |
16 cores |
32 GB |
256 GB |
3,000 |
1 Gbps |
Medium AIO |
100 |
24 cores |
48 GB |
512 GB |
5,000 |
2 x 1 Gbps |
Large AIO |
250 |
32 cores |
64 GB |
1,024 GB |
10,000 |
2 x 10 Gbps |
1.5. Host for SD-WAN deployment
To deploy and update the management components of the solution in High Availability and Distributed Deployment scenarios, you need a dedicated host with the Kaspersky Deployment Toolkit (KDT).
Table 5. KDT instance type definitions
Deployment scenario |
Specifications (approximate) |
||||
CPU* |
RAM |
Storage size** |
Storage IOPS** |
Network adapter |
|
High Availability and Distributed Deployment |
8 cores |
16 GB |
512 GB |
5,000 |
1 Gbps |
* CPU without Hyper-Threading. Recommendations:
- Xeon Silver 4309Y for KDT instances
** SSD
2. Administration system deployment scenarios
2.1. Standalone deployment
The standalone deployment scenario of the Kaspersky SD-WAN administration system is intended for demonstration purposes only and is not recommended for a production environment.
2.2. High Availability deployment
Deploying the Kaspersky SD-WAN administration system in a High Availability (HA) scenario requires three AIO instances (HA3). The hardware requirements of the instances are specified in Table 4. The following table lists sizing recommendations for HA3 deployment.
Table 6. Requirements of instances for HA3 deployment
Number of CPE devices |
HA3 instance |
50 |
3 x Small AIO |
100 |
3 x Medium AIO |
250 |
3 x Large AIO |
2.3. Distributed Deployment
Deploying the Kaspersky SD-WAN administration system in a Distributed Deployment scenario requires three dedicated ORC instances, three dedicated CTL instances, three dedicated MON instances, and one KDT host.
Table 7. Requirements of instances for deployment
Number of CPE devices |
ORC |
CTL |
MON |
KDT |
250 |
3 x Small ORC |
3 x Small CTL |
3 x Small MON |
1 x KDT |
500 |
3 x Small ORC |
3 x Medium CTL |
3 x Small MON |
1 x KDT |
1,000 |
3 x Small ORC |
3 x Large CTL |
3 x Small MON |
1 x KDT |
2,500 |
3 x Small ORC |
15 x Medium CTL |
3 x Small MON |
1 x KDT |
5,000 |
3 x Medium ORC |
30 x Medium CTL |
3 x Medium MON |
1 x KDT |
7,500 |
3 x Medium ORC |
45 x Medium CTL |
3 x Medium MON |
1 x KDT |
10,000 |
3 x Large ORC |
60 x Medium CTL |
3 x Large MON |
1 x KDT |
20,000 |
6 x Large ORC |
120 x Medium CTL |
6 x Large MON |
1 x KDT |
25,000 |
9 x Large ORC |
150 x Medium CTL |
9 x Large MON |
1 x KDT |
3. Third-party solution requirements
The following third-party solutions are required to deploy Kaspersky SD-WAN:
- The Zabbix monitoring system versions 5.0.26 or 6.0.0. For details, please refer to the official documentation of the Zabbix solution.
- The Docker cloud platform version 1.5 or later for deploying Docker containers of solution components. For details, please refer to the official documentation of the Docker cloud platform.
- The OpenStreetMap service for viewing the transport service topology overlaid on a map. If the infrastructure of your organization does not provide for an Internet connection, you can use offline maps. Offline maps take up additional disk space:
- The offline map (central-fed-district-latest.osm.pbf) takes up approximately 100 GB.
- Geocoding data takes up approximately 10 GB.
For detailed information, please refer to the official documentation of the OpenStreetMap service.
Operating system requirements
The following 64-bit operating systems are supported:
- Ubuntu 22.04 LTS.
- Astra Linux 1.7 (security level: "Orel").
- RED OS 7.3 "MUROM".
Requirements for links between nodes of solution components
When deploying Kaspersky SD-WAN, you can deploy multiple nodes of solution components. The following requirements apply to links between nodes of solution components:
- Requirements for links between controller nodes:
- Bandwidth: 1 Gbps
- RTT (Round Trip Time): 200 ms or less
- Packet loss: 0%
- Requirements for links between MongoDB database nodes:
- Bandwidth: 1 Gbps
- RTT: 50 ms or less
- Packet loss: 0%
- Requirements for links between Redis database nodes:
- Bandwidth: 1 Mbps
- RTT: 50 ms or less
- Packet loss: 0%
Browser requirements
The following browsers are supported for managing the orchestrator web interface:
- Google Chrome 100 or later
- Firefox 100 or later
- Microsoft Edge 100 or later
- Opera 90 or later
- Safari 15 or later
Operating system:
Ubuntu 20.04 LTS or 22.04 LTS
RED OS 8
The operating system must support internet access or contain a mounted disk image.
4 virtual CPU cores.
8 GB of RAM.
32 GB of free disk space.
The name and password of root accounts must be the same on the administrator device and on the virtual machines or physical servers on which you want to deploy the solution components. //Hidden, will remove or rewrite this later
CPE device requirements
The following CPE device models are supported:
- KESR-M1-R-5G-2L-W
- KESR-M2-K-5G-1L-W
- KESR-M2-K-5G-1S
- KESR-M3-K-4G-4S
- KESR-M4-K-2X-1CPU
- KESR-M4-K-8G-4X-1CPU
- KESR-M5-K-8G-4X-2CPU
- KESR-M5-K-8X-2CPU
CPE devices of the KESR model are based on x86 (Intel 80x86) and MIPS (Microprocessor without Interlocked Pipeline Stages) processor architectures.
KESR M3–M5 CPE devices have Intel network adapters that are compatible with Intel SFP transceivers. For details about supported SFP transceivers, you can use the Intel Product Compatibility Tool
(in the territory of the Russian Federation, the link is accessible only via VPN). When using the Intel Product Compatibility Tool, you need to select one of the following product categories:- 500 Series to view SFP transceivers that are compatible with KESR M3 CPE devices.
- 700 Series to view SFP transceivers that are compatible with KESR M4–M5 CPE devices.
Kaspersky experts carried out tests to confirm the functionality of CPE devices when providing the L3 VPN service (see the table below). DPI (Deep Packet Inspection) was not used on the tested devices, and traffic encryption was disabled.
Model |
Packet size (bytes) |
Bandwidth (Mbps) |
|---|---|---|
KESR-M1 |
IMIX (417) |
30 |
Large (1300) |
115 |
|
KESR-M2 |
IMIX (417) |
165 |
Large (1300) |
241 |
|
KESR-M3 |
IMIX (417) |
805 |
Large (1300) |
1150 |
|
KESR-M4 |
IMIX (417) |
1430 |
Large (1300) |
2870 |
For detailed information about the characteristics of CPE devices, please refer to the official page of the solution.
You can deploy uCPE devices on servers with x86 (Intel 80x86) or ARM64 processor architectures.
vCPE device requirements
The distribution kit includes the following firmware for deploying vCPE devices:
- vKESR-M1
- vKESR-M2
- vKESR-M3
- vKESR-M4
The following virtualization environments are supported for vCPE devices:
- VMware 7.0 or later
- KVM with kernel version 5.15 or later
Only the original KVM virtualization environment without additional orchestration tools is supported.
The following table lists the virtual resource requirements for deploying vCPE devices.
Firmware |
CPU |
RAM, GB |
Disk, GB |
|---|---|---|---|
vKESR-M1 |
2 |
0.5 |
1 |
vKESR-M2 |
4 |
8 |
1 |
vKESR-M3 |
12 |
16 |
1 |
vKESR-M4 |
24 |
32 |
1 |
When upgrading Kaspersky SD-WAN from version 2.2 to 2.3, you need to make sure that your previously deployed vCPE devices satisfy the requirements of the new version, after which you can update your vCPE devices using the vKESR-M1-5 firmware.
Page topEnsuring security
Security in Kaspersky SD-WAN is ensured in the data plane, control plane, and orchestration plane. The security level of the solution as a whole is determined by the security level of each of these planes, as well as the security of their interaction. The following processes take place in each plane:
- User authentication and authorization
- Use of secure management protocols
- Encryption of control traffic
- Secure connection of CPE devices
Secure management protocols
We recommend using HTTPS when communicating with the SD-WAN network through the orchestrator web interface or API. You can upload your own certificates to the web interface or use automatically generated self-signed certificates. The solution uses several protocols to transmit control traffic to components (see the table below).
Interacting components |
Protocol |
Additional security measures |
Orchestrator and controller |
gRPC |
TLS is used for authentication and traffic encryption between the client and server. |
Orchestrator and CPE device |
HTTPS |
Certificate verification and a token are used for authentication and traffic encryption between the orchestrator and the CPE device. |
Controller and CPE device |
OpenFlow 1.3.4 |
TLS is used for authentication and traffic encryption between the controller and the CPE device. |
Secure connection of CPE devices
The solution uses the following mechanisms for secure connection of CPE devices:
- Discovery of CPE devices by DPIDs (datapath identifiers).
- Deferred registration. You can select the state of the CPE device after successful registration: Enabled or Disabled. A disabled CPE device must be enabled after making sure it is installed at the location.
- Two-factor authentication.
Using virtual network functions
You can provide an additional layer of security with virtual network functions deployed in the data center and/or on
. For example, traffic can be relayed from a CPE device to a virtual network function that acts as a firewall or proxy server. Virtual network functions can perform the following SD-WAN protection functions:- Next-Generation Firewall (NGFW)
- Protection from DDoS (Distributed Denial of Service) attacks
- Intrusion Detection System (IDS) and Intrusion Prevention System (IPS)
- Anti-Virus
- Anti-Spam
- Content Filtering and URL filtering system
- DLP (Data Loss Prevention) system for preventing confidential information leaks
- Secure Web Proxy
What's new
Kaspersky SD-WAN has the following new and improved functionality:
- Integration with Kaspersky KSC/OSMP is supported (with some limitations; see Known limitations below).
- Improved CPE scaling to a cluster of controllers thanks to the Active-Active Multi-Master architecture.
- Added support for Policy-based Routing.
- Static DHCP reservation is supported.
- Connecting a CPE to the controller and orchestrator via a LAN port is now supported.
- Added BGP support for additional VRF tables.
- A CPE can be reset to default settings using a button (for KESR M1–M3 models).
- The graphical interface of the orchestrator has been improved by replacing modal windows with side panes.
- Improved Link State Control mechanism: the controller is asynchronously notified about failure or recovery of tunnel links.
- Firmware metadata now includes its type (OVS/SWOS).
- The controller/orchestrator connectivity status is indicated by an LED on the CPE panel (only for special device versions).
- Reservation of MAC address allocation for overlay interfaces.
- Added the OpenFlow packet prioritizing mechanism.
- The optimized view of tunnels between CPE and controllers now displays full information about links, including the NAT and WAN Disjoint topology attributes.
- The route metric for network interfaces with sdwan0–sdwan3 aliases is assigned automatically: the sdwan0 gets the highest priority, and sdwan3 gets the lowest priority. The Route metric value is blocked for manual editing for interfaces with sdwan0–sdwan9 aliases.
Known limitations
Kaspersky SD-WAN has the following limitations:
- Limitations when integrating the solution with Kaspersky KSC/OSMP:
- Available for new installations only
- SSH console is not supported
- VNC console is not supported
- Firewall rules do not work in user-created virtual routing and forwarding tables.
- When static routes are modified, the FRR daemon is restarted.
- NetFlow flows are not distributed across network interfaces.