Contents
Configuring the gateway
Configuration of data transfer from the OPC UA server to the MQTT broker via Kaspersky IoT Secure Gateway 100 consists of the following steps:
- Generating an encryption key and certificates for connection over the OPC UA protocol
An
and must be generated if a secure connection is used. - Configuring nodes for data transfer over the OPC UA protocol on the OPC UA server
You can read about the OPC UA protocol specification on the developer's website. Kaspersky IoT Secure Gateway 100 version 2.0 supports OPC UA protocol version 1.04.
- Generating an encryption key and certificates for connection over the MQTT protocol
You will need to generate an encryption key and certificate for the
client, and prepare a file containing the that was used to sign the server certificate. - Configuring the Kaspersky IoT Secure Gateway 100 settings for transferring data from the OPC UA server to the MQTT broker
Detailed instructions related to this step are provided in this Help section.
Extracting and inserting a microSD memory card
The microSD card is installed in the microSD slot on the Siemens SIMATIC IOT2040 device and contains the following files:
- configuration files with the settings of Kaspersky IoT Secure Gateway 100
- Kaspersky IoT Secure Gateway 100 health log files
- file with information about third-party code
To access these files, you need to extract the microSD card from the device and connect it to a computer that has a Linux operating system installed. To continue gateway operations, you should re-insert the microSD card into the device.
The Siemens SIMATIC IOT2040 device should be powered off before you extract and install the microSD memory card.
To extract and then re-insert the microSD memory card:
- Open the right-side cover of the device.
- Move the memory card slot tab downwards and open it.
- Extract the microSD card.
- Put the microSD card back, close the tab and move it upwards.
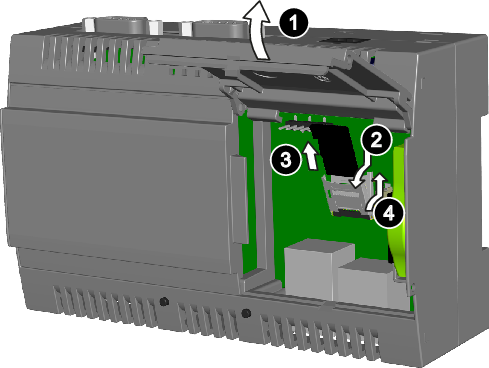
Extracting and inserting a microSD memory card
Location of files on the microSD memory card
To change the settings of Kaspersky IoT Secure Gateway 100, you will need to extract the microSD card from the microSD slot of the Siemens SIMATIC IOT2040 device, connect the microSD card to a computer running a Linux operating system, change the contents of the configuration files, and re-insert the microSD card into the device.
The microSD memory card includes five partitions (see the figure below):
HW-BOOT– contains the boot image of and a text file with information about third-party code.HW-LOG– contains the health log files and the.logfile with the health log settings.HW-IDS– contains the following:- The
OpcUaClientSettings-0.jsonfile with the settings for receiving data over the OPC UA protocol. - The
MqttPublisherSettings-0.jsonfile with the settings for sending data over the MQTT protocol. - Files of certificates and encryption keys.
- The
HW-INW– contains the file with internal network settings.HW-ENW– contains the file with external network settings.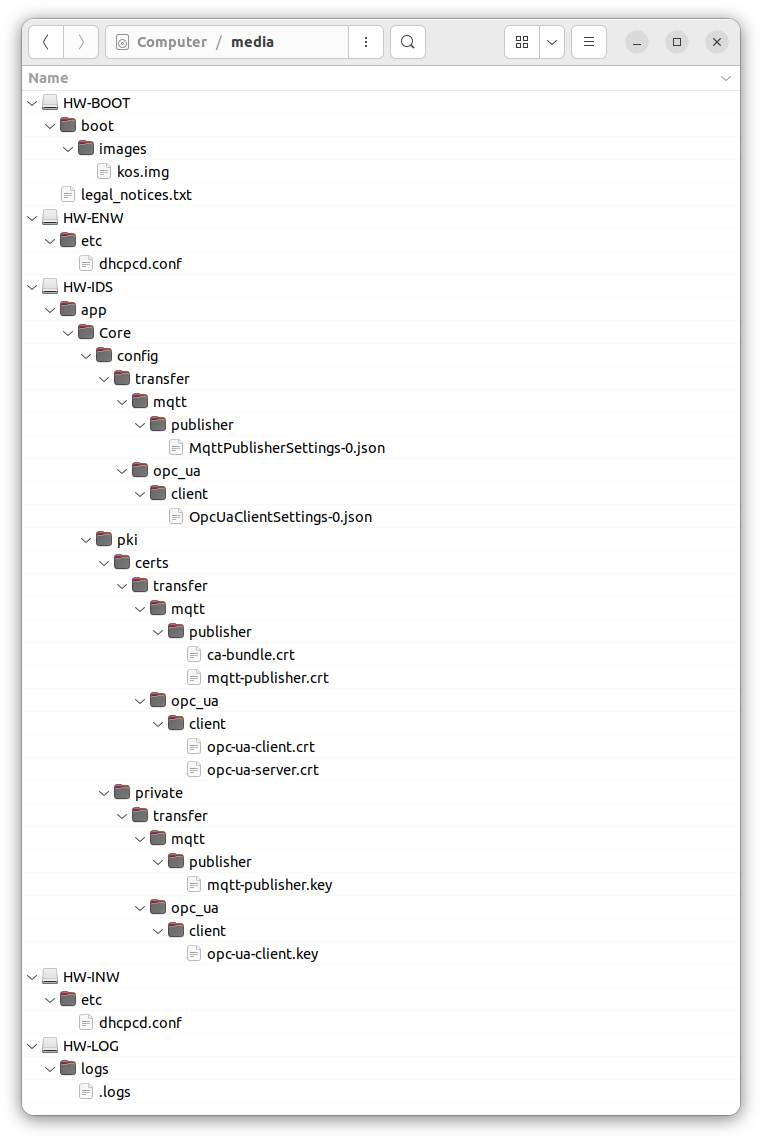
Location of files on the microSD memory card
Connecting to the network and configuring network settings
To connect a device to an external and internal network, you must establish physical connections (using an RJ45 cable) and configure the external and internal network settings if necessary.
Physical connection to the network
To connect Kaspersky IoT Secure Gateway 100 to a data transfer network:
- Connect the network cable of the internal network (where the OPC UA server resides) to the PN/IE LAN X2 P1 port of the device.
- Connect the network cable of the external network (where the resides) to the PN/IE LAN X1 P1 port of the device.
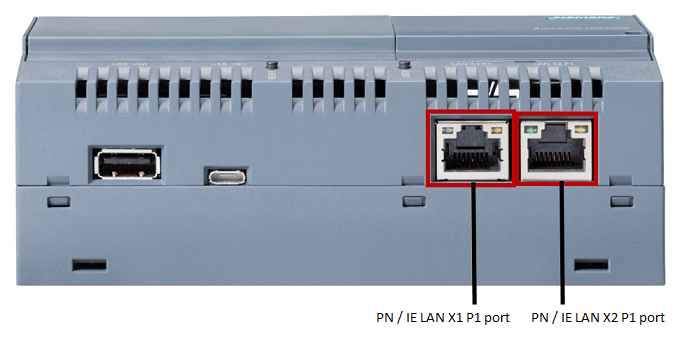
Layout of Ethernet ports on the Siemens SIMATIC IOT2040 device
Automatically obtaining network settings
By default, Kaspersky IoT Secure Gateway 100 is delivered with a dynamic (DHCP) configuration for the internal and external network. To automatically receive network settings in this configuration, there must be a configured DHCP server residing in the same network.
If there is no DHCP server or if you do not want to use dynamic configuration of the network, use a static configuration of the network.
Configuring static network settings
To configure static settings for the external and internal network:
- Create two separate configuration files named
dhcpcd.confon the microSD card:- One for the external network in the directory
/etcon theHW-ENWpartition; - One for the internal network in the directory
/etcon theHW-INWpartition.
- One for the external network in the directory
- In the
dhcpcd.conffiles, define the network settings according to the dhcpd documentation.Sample configuration file defining the settings for an external or internal network:
static ip_address=192.168.1.177/23
static routers=192.168.1.1
- Save the changes.
Configuring a connection over the OPC UA protocol
Kaspersky IoT Secure Gateway 100 receives data from the OPC UA server residing within the internal enterprise network over the OPC UA protocol, which is described by the OPC Unified Architecture specification. You can read about the OPC UA protocol specification on the developer's website. Kaspersky IoT Secure Gateway 100 supports OPC UA protocol version 1.04.
Securing a connection over the OPC UA protocol
To use a secure connection between the OPC UA client and the OPC UA server:
- Copy the OPC UA client certificate to the directory
/app/Core/pki/certs/transfer/opc_ua/clienton theHW-IDSpartition of the microSD card. - Copy the OPC UA server certificate to the directory
/app/Core/pki/certs/transfer/opc_ua/clienton theHW-IDSpartition of the microSD card. - Copy the private encryption key of the OPC UA client to the directory
/app/Core/pki/private/transfer/opc_ua/clienton theHW-IDSpartition of the microSD card.
Data can also be transmitted over the OPC UA protocol without using an encrypted connection. However, a secure connection between the OPC UA client and the OPC UA server cannot be ensured without encryption. It is not recommended to use an unsecured operating mode for Kaspersky IoT Secure Gateway 100.
Page topConfiguring data acquisition over the OPC UA protocol
To configure data acquisition using the OPC UA protocol:
- Create the
OpcUaClientSettings-0.jsonconfiguration file. - In the
OpcUaClientSettings-0.jsonfile, specify the OPC UA settings and their values in accordance with JSON syntax. - Put the configuration file into the directory
/app/Core/config/transfer/opc_ua/clienton theHW-IDSpartition of the microSD card.
Sample configuration file:
OpcUaClientSettings-0.json
{
"id": 0,
"name": "Kaspersky IoT Secure Gateway 100 OPC UA Client",
"description": "Collects data from CNC by Kaspersky IoT Secure Gateway 100",
"url": "opc.tcp://192.168.177.7:4840",
"readingCycle": 1,
"security": {
"mode": "SignAndEncrypt",
"policy": "Basic256Sha256",
"clientPkiData": {
"certificate": "opc-ua-client.crt",
"privateKey": "opc-ua-client.key"
},
"trustList": ["opc-ua-server.crt"]
},
"userCredentials":
{
"username": "KISG100",
"password": "0R20jN#yZd~zaLKe?2J#@~|YC"
},
"heartbeat": {
"id": 0,
"name": "Heartbeat",
"timeout": 60
},
"nodes": [
{
"id": 1,
"name": "Temperature",
"nodeId": "ns=1;s=VariableTemperature"
},
{
"id": 2,
"name": "Speed",
"nodeId": "ns=2;i=2045"
}
]
}
To edit files in JSON format, we recommend using a text editor that supports JSON syntax highlight. This will help avoid potential errors (for example, unbalanced braces).
Parameters description in the OpcUaClientSettings-0.json configuration file
The required parameters should be explicitly defined. The other parameters are optional. For optional parameters that are not included in the configuration file, the default value prescribed by the OPC UA protocol may be used.
Parameters in the OpcUaClientSettings-0.json file
Parameter name |
Required parameter |
Description |
Possible values and notes |
|---|---|---|---|
|
Yes |
ID of the OPC UA client that receives data from the OPC UA server. |
The value of this parameter must match the value of the |
|
Yes |
Name of the OPC UA client that receives data from the OPC UA server. |
Example: |
|
|
Description of the OPC UA client that receives data from the OPC UA server. |
Example: |
|
Yes |
OPC UA server address. |
Example: Port 4840 is used by default. |
|
No |
Gateway data read frequency (in seconds). |
Integer no less than
|
|
Yes |
block. Contains the mode, policy, and trustList parameters, and the clientPkiData parameter block.
|
The If you do not need to configure the security parameters, enter |
|
No |
Mode for managing the security of the client application connection. |
|
|
No |
Name of the used on the OPC UA server. |
The |
|
No |
Parameter block containing the certificate and private encryption key of the OPC UA client for an encrypted connection. |
The For secure communication over OPC UA, you will need to create a private encryption key and certificate and add them to the client and server configuration. When generating certificates for a connection between a client (Kaspersky IoT Secure Gateway 100) and the OPC UA server, make sure that the certificates comply with the following requirements:
|
|
No |
Certificate file name. |
|
|
No |
Private encryption key file name. |
|
|
No |
Array containing the names of trusted certificate files. |
If the OPC UA server configuration prescribes the use of a custom list of trusted certificates, add the client certificate to this list. If certificate verification is not required, enter the |
|
No |
Parameter block containing the account credentials of the OPC UA client on the OPC UA server. |
|
|
No |
Name of the user account for authorization on the OPC UA server. |
|
|
No |
Password of the user account for authorization on the OPC UA server. |
|
|
No |
This parameter block is generated by the OPC UA client. It contains the parameters for the Kaspersky IoT Secure Gateway 100 heartbeat signal. |
If you do not add the |
|
No |
Data node ID. |
|
|
No |
Data node name. |
Example: |
|
No |
Interval (in seconds) between the generation of heartbeat signals. |
An integer no less than |
|
Yes |
Parameter block for data nodes. |
Completed for each data node. The ID and name of data nodes are required for building routes and transmitting data from the OPC UA server to the MQTT broker. |
|
Yes |
ID of the outbound port. |
|
|
Yes |
Name of the outbound port. This name must match the destination port topics parameter block in the MqttPublisherSettings-0.json configuration file.
|
Example: To correctly transfer data from the OPC UA server to the MQTT broker, you need to map the OPC UA to their corresponding MQTT topics. Thename value is used for mapping.
|
|
Yes |
Data node ID. |
|
|
Yes |
ID of the OPC UA server namespace. |
|
|
Yes |
ID of the data node in the OPC UA server namespace. |
Two types of IDs are possible:
|
Special considerations when configuring OPC UA security settings
Kaspersky IoT Secure Gateway 100 does not establish a connection over the OPC UA protocol in the following cases:
- The server does not have a certificate, and an unsafe connection is not allowed.
- The
trustListparameter lacks a defined server certificate, and theAllowAllvalue is not set. - The client certificate, server certificate or encryption keys do not comply with the settings of the selected security policy.
The OPC UA server and client establish an unsafe connection in the following cases:
- The
nullvalue is set for thesecurityanduserCredentialssettings blocks, and the server supports this type of connection. - The
Anyvalue is set for themodeandpolicyfields, and the server offers the choice for an unsafe connection.
Any weakening of the security settings reduces the security of the connection. For example, the following settings reduce the security of a connection over the OPC UA protocol:
- Use of the
nullvalue for thesecuritysettings block will result in the use of a connection without encryption and without a signature. - Use of the
AllowAllvalue for thetrustListfield disables server certificate verification. - Use of the
nullvalue for theuserCredentialssettings block disables the capability to connect to a server by using a username and password. - The
Basic128Rsa15andBasic256values for thepolicyfield are considered to be obsolete in the OPC UA version 1.4 protocol specification because the SHA-1 hashing algorithm is no longer considered to be secure. - Use of the
Nonevalue for thepolicyormodefields will result in the following:- use of a connection without encryption and without a data signature;
- transmission of a plaintext password to the server.
Configuring a connection over the MQTT protocol
Kaspersky IoT Secure Gateway 100 forwards data to the MQTT broker over the MQTT protocol. You can read the MQTT protocol specification on the developer's website. Kaspersky IoT Secure Gateway 100 version 2.0 supports MQTT protocol version 3.1.1.
Securing a connection over the MQTT protocol
To securely transmit data over the MQTT protocol:
- Copy the file containing the certificate chain of the MQTT client (a chain can consist of one leaf certificate of the client) to the directory
/app/Core/pki/certs/transfer/mqtt/publisheron theHW-IDSpartition of the microSD card. - Copy the file containing the certificate chain that was used to form the digital signature to the directory
/app/Core/pki/certs/transfer/mqtt/publisheron theHW-IDSpartition of the microSD card. - Copy the file of the private encryption key of the MQTT client to the directory
/app/Core/pki/private/transfer/mqtt/publisheron theHW-IDSpartition of the microSD card.
The certificates and encryption keys used by the MQTT client must be in PEM format. The key length of the client certificate must be at least 2048 bits.
Page topConfiguring data transmission over the MQTT protocol
To configure data transmission over the MQTT protocol:
- Create the
MqttPublisherSettings-0.jsonfile. - In the
MqttPublisherSettings-0.jsonfile, specify the MQTT settings and their values in accordance with JSON syntax. - Put the configuration file into the directory
/app/Core/config/transfer/mqtt/publisheron theHW-IDSpartition of the microSD card.
Sample configuration file:
MqttPublisherSettings-0.json
{
"id": 0,
"name": "Kaspersky IoT Secure Gateway 100 MQTT Publisher",
"description": "Transfer data to MQTT Broker by Kaspersky IoT Secure Gateway 100",
"clientId": "KISG100",
"serverUri": "ssl://192.168.188.8:8883",
"security": {
"clientPkiData": {
"certificate": "mqtt-publisher.crt",
"privateKey": "mqtt-publisher.key"
},
"trustStore": ["ca-bundle.crt"]
},
"userCredentials":{
"username": "KISG100",
"password": "4vRXE84zsCy8bLQcZi2HH82TmC"
},
"lastWill": {
"topicName": "LastWill",
"message": "LastMessage"
},
"keepAlive": 800,
"qualityOfService": 1,
"topics": [
{
"id": 0,
"name": "Heartbeat",
"topicName": "Heartbeat"
},
{
"id": 1,
"name": "Temperature",
"topicName": "Temperature"
},
{
"id": 2,
"name": "Speed",
"topicName": "Speed"
}
]
}
To edit files in JSON format, we recommend using a text editor that supports JSON syntax highlight. This will help avoid potential errors (for example, unbalanced braces).
Parameters description in the MqttPublisherSettings-0.json configuration file
The required parameters should be explicitly defined. The other parameters are optional. For optional parameters that are not included in the configuration file, the default value prescribed by the MQTT protocol may be used.
Parameters in the MqttPublisherSettings-0.json file
Parameter name |
Required parameter |
Description |
Possible values and notes |
|---|---|---|---|
|
Yes |
ID of the MQTT client that will send data to the MQTT broker. |
The value of this parameter must match the value of the |
|
Yes |
Name of the MQTT client that will send data to the MQTT broker. |
Example: |
|
No |
Description of the MQTT client that will send data to the MQTT broker. |
Example: |
|
No |
Unique identifier of the MQTT client. |
The internal architecture of Kaspersky IoT Secure Gateway 100 involves interaction between a receiving hub and a sending hub. The The |
|
Yes |
Address of the server that the MQTT client will connect to. |
Example:
|
|
Yes |
Parameter block for configuring a secure connection. Contains the |
The |
|
Yes |
Parameter block containing the names of the certificate and private encryption key files of the MQTT client for an encrypted connection. |
|
|
Yes |
Name of the file containing the certificate chain to the MQTT client certificate. |
|
|
Yes |
Private encryption key file name. |
The key length must be at least 2048 bits. |
|
Yes |
Array that includes the name of the file containing the certificate chain to the MQTT broker certificate. |
Name of the file containing the certificate chain to the certificate of the Certification Authority that signed the MQTT broker certificate. |
|
Yes |
Parameter block responsible for authentication of the MQTT client on the server. |
|
|
No |
Name of the user account for authorization on the MQTT server. |
|
|
No |
Password of the user account for authorization on the MQTT server. |
|
|
No |
Parameter block for configuring a message informing that the client was improperly disconnected (LWT message). |
The client can specify the LWT message when connecting to the MQTT broker for the first time. The MQTT broker will store this message until it detects an improper disconnection of the client. Upon detection of an improper connection, it will send the LWT message to all clients that have subscribed to this type of message. The MQTT broker does not send this message when the client is properly disconnected. |
|
No |
Name of the MQTT topic that determines the information channel where the LWT message will be published. |
Example: |
|
No |
Contents of the LWT message. |
Example: |
|
No |
Period of time that the MQTT broker can wait to receive a message from the MQTT client before terminating the connection due to inactivity. |
The default value is Available values: If the If the server deems a client to be inactive or if the client is not responding to queries, the server can disconnect the client at any time, irrespective of the |
|
No |
Parameter defining a guarantee to send messages. |
Agreement between the message sender (publisher) and message recipient (subscriber) that defines a guarantee to deliver a specific message. The MQTT specification defines the following three levels of
The default value is |
|
Yes |
Array from the parameter blocks of MQTT topics. |
Array of A separate parameter block in the array is completed for each MQTT topic. |
|
Yes |
ID of the destination port. |
Example: |
|
Yes |
Name of the destination port. This name must match the outbound port |
Example: To correctly transfer data from the OPC UA server to the MQTT broker, you need to map the MQTT topics to their corresponding OPC UA data nodes. The |
|
Yes |
Name of the MQTT topic. |
Example: See also: Special considerations when generating names of MQTT topics. |
Special considerations when generating names of MQTT topics
When filling in the values for topicName, please adhere to the following guidelines:
- Wildcard characters cannot be used in the names of MQTT topics. We also do not recommend using the
$character in the names of MQTT topics. - The name of an MQTT topic cannot be blank (it must contain at least one character).
- The names of MQTT topics are case sensitive.
- The names of MQTT topics can contain a blank space character.
- MQTT topics that are separated by only a
/character at the beginning or end of the name are considered to be different MQTT topics. - An MQTT topic name consisting of only a
/character is permitted. - The name of an MQTT topic must not contain the null character (NUL).
- Names of MQTT topics are UTF-8 strings of size that does not exceed 65535 bytes.
Required actions when an MQTT broker certificate is revoked
When an MQTT broker certificate is revoked, you will need to obtain a new certificate from the MQTT broker administrator and replace the revoked certificate. If you do not do this, Kaspersky IoT Secure Gateway 100 will trust both the revoked certificate and the new certificate until the revoked certificate expires. This could lead to a situation in which a connection established over a secure channel is not actually secure.
To use a new MQTT broker certificate instead of a revoked certificate:
- In the
/app/Core/pki/certs/transfer/mqtt/publisherdirectory on theHW-IDSpartition of the microSD card, delete the file indicated in thetrustStoreparameter of the MqttPublisherSettings-0.json configuration file. - In the
trustStoreparameter of theMqttPublisherSettings-0.jsonconfiguration file, specify the name of the new certificate file. - Copy the new certificate file to the
/app/Core/pki/certs/transfer/mqtt/publisherdirectory on theHW-IDSpartition.